- Cryptocurrency
- February 10, 2026
Table of Contents
You bought a hardware wallet because you wanted to be safe. You followed the advice to move your crypto off exchanges and into cold storage. What no one tells you is that scammers now target hardware crypto wallets just as aggressively as online platforms.
Today, hardware crypto wallet scams are one of the fastest-growing forms of crypto fraud. Fake devices, pre-filled recovery phrases, cloned manufacturer websites, and wallet drainer attacks are tricking even experienced investors. These scams don’t rely on hacking the blockchain; they rely on manipulating people.
In this guide, you’ll learn how hardware wallet scams work, the most common traps to avoid, and what to do if your crypto has already been stolen.
What Are Hardware Crypto Wallet Scams?
Hardware crypto wallet scams happen when criminals tamper with a device, manipulate the setup process, or trick users into revealing their recovery phrases.
Instead of attacking the blockchain itself, scammers focus on the person behind the wallet. These scams often begin before you even turn on the device. Some wallets are sold already “set up,” while others include fake instructions that guide users to use a pre-filled seed phrase. In other cases, victims are sent to fake websites that look like official wallet brands and are asked to enter their recovery phrase to “verify” or “fix” their wallet.
Once a scammer gets access to your recovery phrase, they gain full control of your crypto. Your hardware wallet may still be in your hands, but the funds can be drained at any time, often without warning.
Who Is Most at Risk of Hardware Wallet Scams?
- First-time hardware wallet buyers who aren’t yet familiar with proper setup and may trust pre-filled seed phrases or unofficial instructions
- People buying from marketplaces or resellers, where devices may be opened, pre-activated, or tampered with before delivery
- DeFi, NFT, and airdrop users who frequently connect wallets to new platforms and may unknowingly approve malicious transactions
- Victims of previous crypto scams, who are often targeted again through fake recovery services or support impersonation
- Anyone acting under urgency, such as responding to “security alerts,” recalls, or limited-time offers, without verifying the source
Because these attacks rely on deception rather than technology, they affect both beginners and experienced crypto users. The wallet itself isn’t broken; the trust behind it is.
Most Common Hardware Crypto Wallet Scams
The scam of hardware crypto wallets tends to have a predictable pattern. Although the devices are developed to be safe, the fraudsters target the misuse of the purchase process, configuration, or the actions of the users. The table below is a breakdown of the most frequent hardware wallet scams, their operation, and why they are so dangerous.
|
Scam Type |
How the Scam Works |
Why It’s Dangerous |
|
Pre-Activated / Tampered Hardware Wallets |
Scammers sell wallets that have already been opened and initialized. The attacker creates the seed phrase before shipping the device. |
The scammer already controls the wallet. Funds are stolen as soon as crypto is deposited. |
|
Pre-Filled or Malicious Seed Phrase Scams |
The wallet includes a printed or scratch-off recovery phrase and instructions to use it during setup. |
Legitimate wallets never provide seed phrases. Using one gives scammers full access. |
|
Fake Hardware Wallet Websites |
Victims are redirected to websites that look like official wallet brands and are asked to enter recovery phrases or download software. |
Seed phrases are captured instantly, compromising the wallet completely. |
|
Fake Support & Customer Service Impersonation |
Scammers pose as wallet support agents and request recovery phrases to “fix” or “verify” a device. |
No real support service will ever ask for a seed phrase. Funds are drained soon after. |
|
Fake Companion Apps & Browser Extensions |
Malicious apps or extensions mimic official wallet software and trick users during connection or setup. |
Users unknowingly approve malicious actions or expose private data. |
|
“Defective Device” Replacement Scams |
Victims are told their wallet is faulty or recalled and receive a fake replacement device. |
Replacement wallets are pre-configured to steal funds after migration. |
|
Wallet Drainer & Malicious dApp Connections |
Users connect a real hardware wallet to a fake site and sign transactions, granting token permissions. |
Assets are drained without sharing the seed phrase, confusing many victims. |
|
Seed Phrase Phishing (Digital or Physical) |
Users are tricked into typing or storing their 12–24 word phrases on websites, forms, or files. |
This immediately destroys cold storage protection and exposes all assets. |
Hardware wallet scams don’t usually involve hacking the device. They involve manipulating people. Now that you’ve seen the most common scams, let’s look at how they work in real life.
How Hardware Crypto Wallet Scams Work?
Hardware crypto wallet scams rarely feel like scams at the beginning. In most cases, everything looks normal, professional, and secure. Instead of attacking the technology itself, scammers focus on how people buy, set up, and use their hardware wallets.
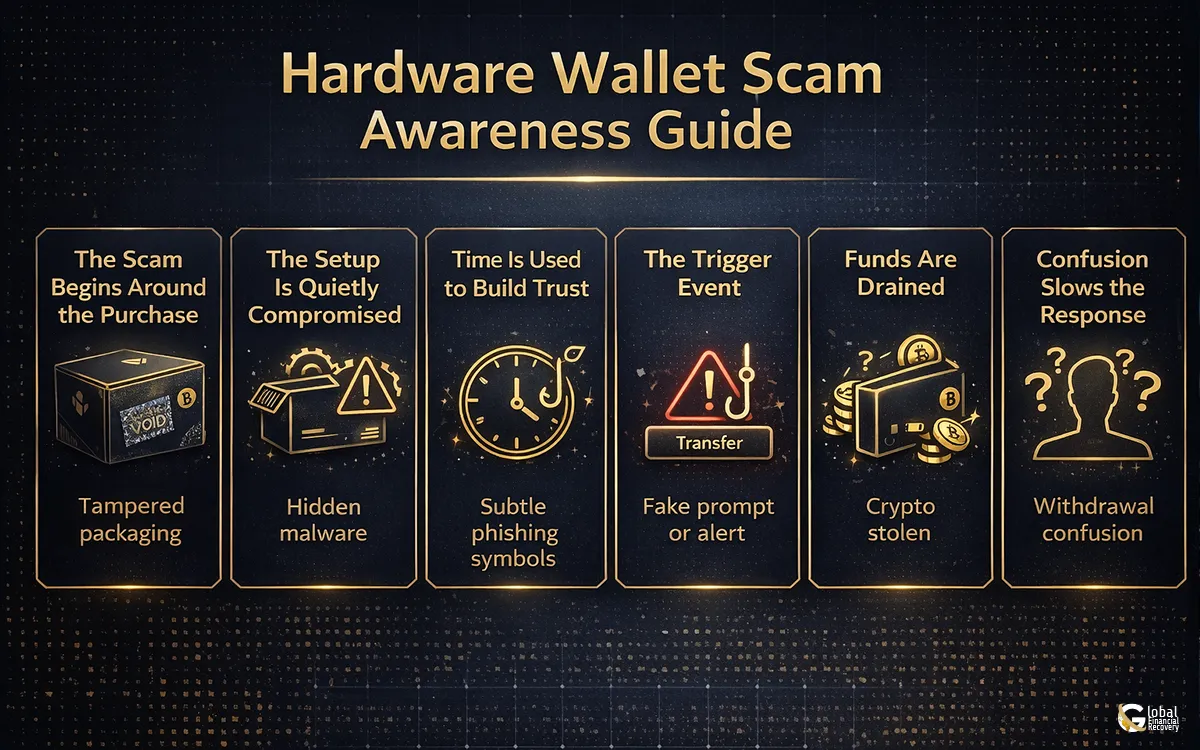
Step 1: The Scam Begins Around the Purchase
This usually begins prior to the wallet being utilized. The victims can purchase the device on an unofficial website, from a third-party seller, or at a very low price. In other instances, the scammers will contact the purchaser after purchase by saying that there is a security problem, recall, or defect that requires immediate attention.
Step 2: The Setup Is Quietly Compromised
During setup, the scam is locked in. Victims may be told to use a pre-generated recovery phrase, follow instructions from a fake website, or install software that looks official but isn’t. Because the wallet works normally, users believe their crypto is secure even though the scammer already has access.
Step 3: Time Is Used to Build Trust
Scammers rarely act immediately. The wallet continues to work as expected, showing correct balances and processing small transactions. This builds confidence and encourages larger deposits.
Step 4: The Trigger Event
Once enough value is stored, the theft begins. This may happen after a large deposit, a malicious website connection, or the approval of a dangerous transaction.
Step 5: Funds Are Drained
Crypto is moved out quickly, often split across multiple wallets to make tracking harder. Victims usually notice only after the transaction is confirmed on the blockchain.
Step 6: Confusion Slows the Response
Many people assume a technical error or a user mistake. This delay gives scammers more time to hide stolen crypto. Acting quickly greatly improves the chances of recovery.
Hardware crypto wallet scams succeed because they exploit trust, not broken security. Once you understand the process, the warning signs become much easier to spot.
Warning Signs Your Hardware Wallet Has Been Compromised
The majority of individuals do not notice that their hardware wallet has been attacked immediately. This is because hardware crypto wallet fraud can be a silent background activity. Nevertheless, the first indications of something wrong are subtle. If even one of the signs below feels familiar, it’s worth taking it seriously.

-
Funds Move Without You Doing Anything
The most important red flag is seeing crypto leave your wallet when you didn’t approve a transaction. Sometimes it happens all at once. Other times, small amounts disappear first, which makes the loss easier to overlook.
A legitimate hardware wallet cannot move funds on its own. If this happens, access has already been compromised.
-
Your Wallet Worked Fine - Until It Didn’t
Many victims say the same thing: “Everything worked normally at first.” That’s intentional. Scammers often wait days or weeks before acting, so you feel confident storing more crypto.
If your wallet suddenly behaves differently after a period of normal use, it may be a sign that the setup was compromised from the start.
-
You’re Asked for Your Recovery Phrase, Anywhere
This is never normal. No hardware wallet manufacturer, update process, or support agent will ever ask for your 12- or 24-word recovery phrase.
If you entered your seed phrase into a website, app, form, or computer file even once, your wallet should be considered compromised.
-
Unexpected “Security Alerts” or Support Messages
Emails or messages claiming urgent security problems, firmware failures, or device recalls are a common tactic in hardware wallet scams. These messages often push you to act quickly, before you have time to verify the source.
Urgency is a manipulation tool. Legitimate wallet providers do not pressure users to share sensitive information.
-
Your Recovery Phrase Suddenly Doesn’t Work
If your recovery phrase fails during a legitimate recovery attempt, it could mean the wallet was pre-configured or altered before you received it. In some scams, victims were never the true owners of the wallet at all.
This is especially common with pre-activated or tampered hardware wallets.
-
Tokens Disappear After Connecting to a Website or dApp
If your wallet was connected to a website and tokens were later drained, you may have unknowingly approved a malicious transaction. These “wallet drainer” scams don’t require your seed phrase, which makes them confusing and dangerous. The wallet itself may still function, but permissions were already granted.
Why These Signs Are Often Missed
Hardware wallets create a strong sense of safety. Because the device feels secure, many people assume losses must be a mistake or a technical glitch. Unfortunately, that delay gives scammers more time to move and hide stolen crypto. When it comes to hardware crypto wallet scams, early action makes a real difference.
Notable Real-World Case: $282 Million Lost in a Hardware Wallet Scam
In one of the largest reported incidents of its kind, a cryptocurrency holder lost approximately $282 million worth of Bitcoin and Litecoin after being tricked in a hardware wallet social engineering attack on January 10, 2026. In this case, the scam did not involve hacking the wallet’s technology; instead, the attacker impersonated trusted support, convinced the victim to reveal their recovery seed phrase, and then restored the wallet on their own device before draining all funds. The stolen crypto was rapidly converted into privacy-focused assets like Monero and routed across multiple networks to obscure the trail, highlighting just how effective social engineering can be even against supposedly secure cold storage.
What to Do If Your Hardware Wallet Is Compromised

When you learn that your hardware wallet has been compromised, it can be very scary. However, there are steps that you can take that will help you.
First of all, you must stop using your wallet. This means that you should disconnect it from all websites, apps, and devices. This will help you avoid any loss of money due to approvals, wallet draining, or even phishing connections.
In addition, it is important that you never use your recovery phrase again if it was compromised, pre-filled, or entered anywhere online. This is because anyone who knows this phrase will have access to your wallet remotely.
Therefore, it would be best that you create a new wallet on a device that you trust and generate a new phrase. You should then proceed to transfer your crypto only once. You should also save all evidence of the scam, including wallet addresses, transaction IDs, screenshots, emails, and even links from the scam websites. These will all be very important when it comes to crypto scam recovery.
Hardware Wallet Security Is About Awareness, Not Just Devices
Hardware wallets offer strong protection, but they can’t prevent mistakes caused by urgency or misplaced trust. That’s why most hardware wallet scams target people, not technology.
Knowing how these scams work is your best defense, and if your crypto has been stolen, Global Financial Recovery can help you take the next step with confidence.
FAQs (Frequently Asked Questions)
Yes. A wallet can look factory-sealed and still be compromised if it was opened or altered before reaching you. Some scams use pre-activated wallets where the attacker already controls the recovery phrase.
Hardware wallets can’t judge intent. If a scam tricks you into approving access, such as signing a malicious permission, the wallet will still process the action.
Only if you generated it yourself and never shared or reused it. Seed phrases become dangerous when they are pre-printed, photographed, stored digitally, or typed online.
Scammers delay the theft to build trust and encourage larger deposits. Once enough value is stored, they drain the wallet quickly.
No. Blockchain tracing can reveal where funds moved and help support crypto scam recovery efforts.