- Cryptocurrency
- February 18, 2026
Table of Contents
Fake crypto token scams are becoming more common as more people start using cryptocurrencies. These scams usually involve fake tokens that look real but are created only to trick users into sending money or connecting their wallets. Once the scammer gets access, the funds are often gone for good.
The number of fake tokens being made by scammers is rising due to the ease and low cost of starting a new token. They capitalize on trending coins, popular blockchain networks, and the hype surrounding new crypto projects as well. Most of the fake tokens are popularized via social media, messaging programs, or even fake websites that look professional and reliable.
In this guide, you will find out what fake crypto token scams are, how these cryptocurrency scams operate, and the red flags to be cautious of. You will also be informed about the basic measures that you can undertake to save your wallet and not transfer crypto to fake tokens.
What Are Fake Crypto Token Scams?
Fake crypto tokens are created by people who commit financial crimes and copy actual cryptocurrencies. The similarity of such tokens to common coins, names, logos, or even the design of a website, which can be easily confused with the actual one.
Fraudsters frequently replicate well-known cryptocurrency initiatives to mislead users into purchasing or transferring tokens. They can rely on social media content, fake announcements, or even chat applications to make the scam seem real. A lot of individuals become victims of these frauds because everything appears real on the surface.
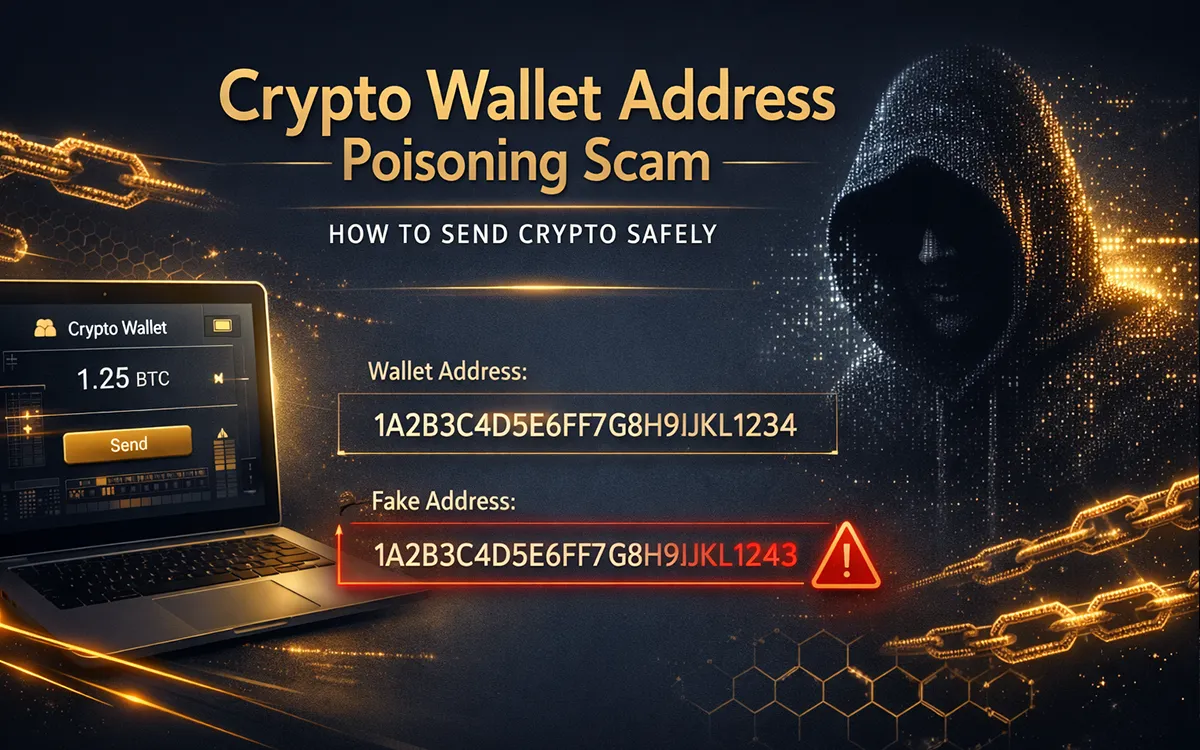
Once money is sent to a fake token, it’s usually very hard, or even impossible, to get it back. Crypto transactions are permanent and cannot be reversed, which is why protecting your wallet before sending any funds is so important.
5 Common Types of Fake Crypto Token Scams
Fake crypto token scams may look different on the surface, but they follow similar patterns. Scammers create fake tokens, build false trust, and push people to act quickly. Below are the most common types of fake token scams seen in crypto recovery cases.

-
Fake Token Presale Scams
A fake presale scam markets a digital token prior to its introduction. Fraudsters state that there will be special prices, bonuses, or guaranteed growth for the first buyers of the token when the latter becomes public. The site is frequently professional, having a whitepaper, roadmap, and countdown timer to generate pressure. The victims have to send crypto directly to a wallet address or link their wallet to get involved. Once payment is made, the token is of no real value, can never be traded, or cannot be delivered at all. The project gets lost, and one cannot get the money back in the regular ways.
-
Fake Crypto Token Investment Scams
In this form of scam, scammers will use a false token as a high-return investment option. They can contact victims over social media, messaging apps, or even dating websites,s posing as seasoned traders or project insiders. Credibility is built by the use of fake profit screenshots and edited charts. The victims are made to invest in a hurry to lock in profits. After the money has been transferred, the token may either be in the full control of the scammer or not be listed in any actual exchange. Although there may be a balance in a site, the money is not withdrawn, and the money invested is lost.
-
Pump and Dump Crypto Schemes
A pump and dump scenario begins when fraudsters purchase low volumes of a low-priced token in large quantities. Then they generate hype on the same by promoting positive news, insider knowledge, or rumours of significant alliances. The price increases rapidly as the number of buyers increases. This is such a rapid expansion that it draws further investors who do not want to be left behind. By the time the price is highest, the scammers sell their possession within a short time. The price drops in minutes, and ordinary investors are left with tokens that are of little or no use.
-
Token Migration and Upgrade Scams
The token migration and upgrade scams fool a user into thinking that the current tokens have to be replaced with a new version. Scammers state that there was a technical update or a change to the blockchain and tell them that they will lose money if they do not act. The victims receive links to websites that resemble official-looking ones and are requested to link their wallets to carry out the migration. Factually, the approval authorises scammers to get access to the wallet. The fraudsters steal the assets on the spot as opposed to refining tokens.
-
Crypto Swap and Airdrop Scams
With swap and airdrop scams, counterfeit tokens are abruptly added to a user’s wallet, or the victim is lured with free rewards. Curious users attempt to swap the token and are redirected to fake swap sites designed to look legitimate. Once the wallet is connected and a transaction is approved, a malicious smart contract gains access to the funds. Assets are transferred within seconds, the promised exchange never happens, and the wallet balance drops without warning.
Although fake crypto token scams take many forms, the underlying tactics of confusion, urgency, and trust remain the same. Victims often don’t realize they have interacted with a scam, which makes understanding fake crypto airdrops an essential step in protecting digital assets. Recognizing how these tokens appear in wallets helps users identify threats before financial damage occurs.
How Fake Tokens End Up in Your Wallet
Many people assume that if a token can be found in their wallet, it must be true. Badly enough, that is not the case with crypto. There are various ways in which fake tokens can find their way into wallets, and the user may never be quite aware of how this occurred.
-
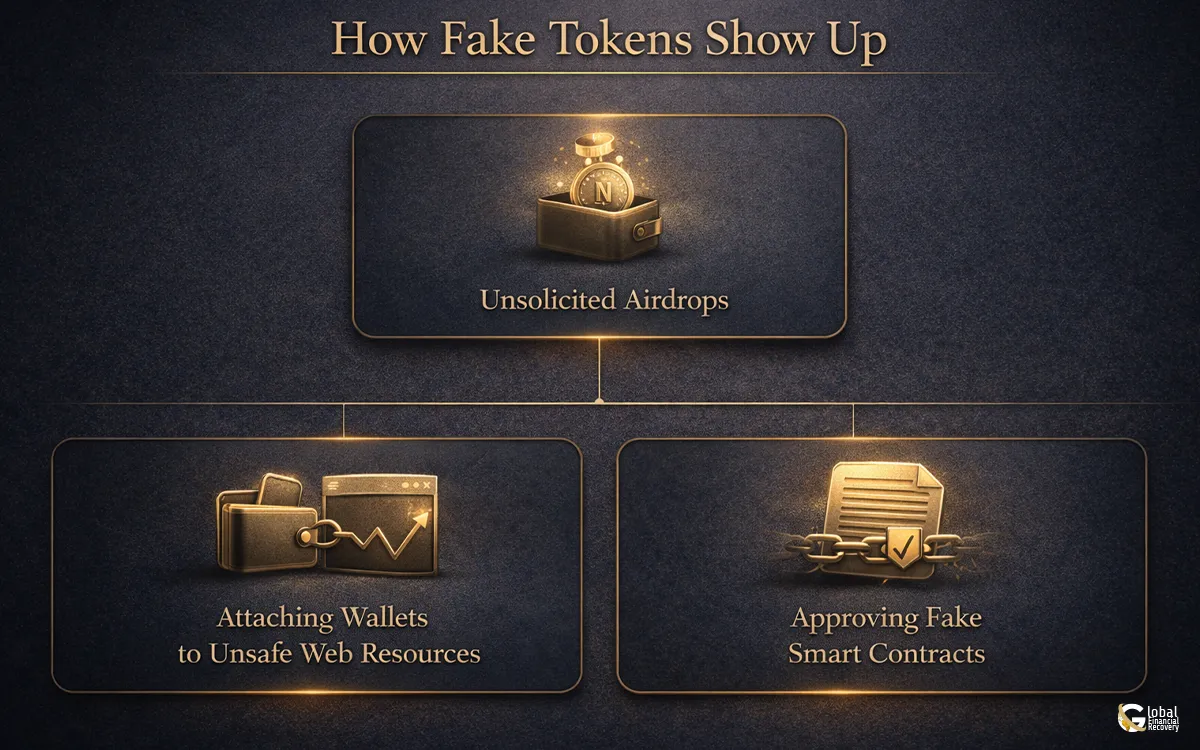
Unsolicited Airdrops
Scammers can occasionally send fake tokens directly to unauthorized wallets. This is what is referred to as an unsolicited airdrop. The token is represented in the wallet as any other asset. Curious users can either click on it, search it, or attempt to trade it in. This is precisely what scammers desire since most users are usually taken to malicious websites.
-
Attaching Wallets to Unsafe Web Resources
Fake tokens are often associated with fraudulent websites that are ready to sell swaps, rewards, or token information. By linking their wallets to these websites, users can be unaware of giving the fraudsters access to their money. These are typical tricks in more extensive fake crypto wallet scams, where the wallet itself is the target.
-
Approving Fake Smart Contracts
Others request that their users approve a transaction before they are able to sell or trade a token. Such approvals might appear innocent, but have the ability to give the scam artists power over the wallet or particular assets. When approved, the funds may be drained without any further input from the user.
A Token in Your Wallet Isn’t Always Real
Crypto wallets do not verify whether a token is real or safe. They simply display anything sent to your wallet address. This means anyone can create a token and send it to any wallet, without permission.
Many fake tokens have no real value. They are not backed by a legitimate project, are not listed on trusted exchanges, and cannot be safely traded. Some exist only to appear in wallets and attract attention.
In many cases, these tokens are used as bait. When users try to learn more, sell, or swap them, they are pushed toward unsafe websites or fake transactions that can lead to further losses.
Seeing a token in your wallet does not confirm ownership, value, or legitimacy. Interacting with an unknown token can put your funds at risk.
Key Warning Signs That a Crypto Token May Be Fake
Fake crypto tokens often look convincing at first glance. However, there are common warning signs that appear again and again in scam cases. Knowing these signs can help you avoid interacting with a fake token before further damage is done.
-
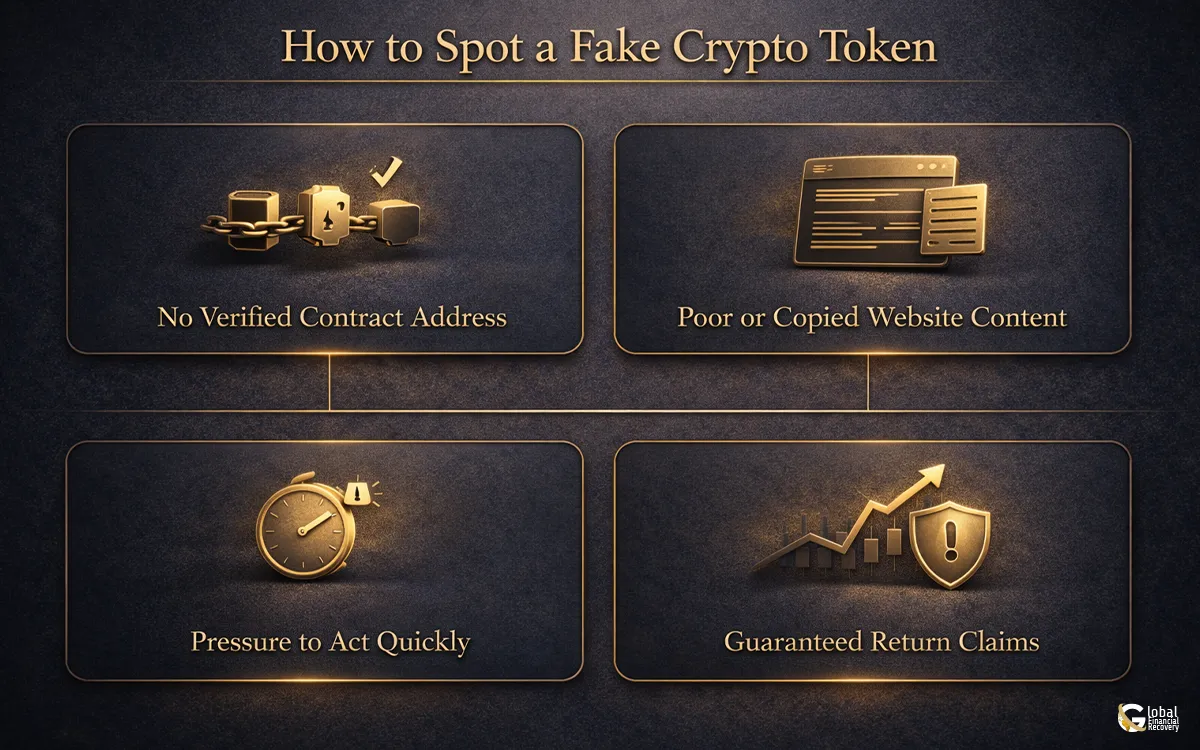
No Verified Contract Address
Trusted blockchain explorers are websites that verify the address of a legitimate crypto token and allow checking it. False tokens tend to conceal such information or give links that are not within records.
When the contract address of a token cannot be verified easily using trusted sources, then it is important to handle it carefully.
-
Poor or Copied Website Content
Numerous counterfeit token websites seem to be very professional at first sight, but have no depth. The content can be of poor writing; it can be copied from other projects or filled with empty assertions and buzzwords.
One of the common indicators that the project is not genuine is the absence of team details, vague project objectives, and broken links.
-
Pressure to Act Quickly
Fraudsters tend to instill a sense of urgency so that people do not take time to think. You can be informed that the offer is closing in the near future or that you need to act as soon as possible to not lose access.
Bona fide crypto projects will not urge the user to make hasty decisions.
-
Guaranteed Return Claims
None of the crypto investments can guarantee profits. There are the alleged fixed returns, risk-free returns, or guaranteed returns, and this is a big warning signal.
These are promises that create some illusion and encourage users to initiate a funds transfer without due diligence.
How to Protect Your Wallet from Fake Crypto Token Scams
While no wallet is completely risk-free, simple habits can greatly reduce your chances of falling for a fake crypto token scam. The steps below are practical and used widely by experienced crypto users.
-
Verify Token Contract Addresses from Official Sources
Always check a token’s contract address using the project’s official website or verified social channels. Compare this address with trusted blockchain explorers before interacting with the token.
If the contract address cannot be confirmed, avoid taking any action.
-
Avoid Interacting With Unknown Tokens
If a token appears in your wallet and you do not recognise it, do not click on it, trade it, or search for it online.
Unknown tokens are often used as bait to push users toward unsafe websites or fake transactions.
-
Do Not Approve Random Swaps or Upgrades
Never approve swaps, migrations, or upgrades unless they are clearly announced through official project channels.
Scammers often use fake upgrades to trick users into approving transactions that give them wallet access.
-
Use Separate Wallets for Trading and Storage
Using one wallet for daily trading and another for long-term storage helps limit damage if something goes wrong.
Even if a trading wallet is compromised, your main funds remain protected.
-
Regularly Review and Revoke Token Permissions
Over time, wallets accumulate permissions granted to different tokens and platforms. Some of these approvals may no longer be needed.
Reviewing and revoking unused permissions reduces the risk of unauthorised access.
What to Do If You’ve Been Targeted by a Fake Token Scam
If you believe you’ve interacted with a fake crypto token, acting quickly can help limit further losses. The steps below focus on protecting your wallet and preserving information that may be useful later.
-
Stop Interacting With the Token
Do not click on the token, attempt to swap it, or follow any links associated with it. Continued interaction can expose your wallet to additional risks.
-
Revoke Approvals Immediately
If you approved any transactions or smart contracts, revoke those permissions as soon as possible. This can prevent further unauthorised access to your wallet.
-
Move Remaining Funds to a Secure Wallet
If your wallet may be compromised, transfer your remaining funds to a new, secure wallet. Use a wallet that has not been connected to unknown websites or tokens.
-
Save Transaction Details and Wallet Addresses
Keep records of transaction IDs, wallet addresses, contract addresses, and any messages or websites linked to the scam. This information is important for investigations and recovery efforts.
-
Consider Professional Help for Crypto Scam Recovery
Fake token scams can be complex, especially when funds have already been moved across multiple wallets. In such cases, working with professionals who specialize in cryptocurrency scam recovery can help you understand what happened and what recovery options may still be available.
Reputable service providers, such as Global Financial Recovery, focus on blockchain analysis and tracing rather than quick promises. Seeking professional guidance can provide clarity and direction during an otherwise stressful situation.
The Risks and Realities of Fake Crypto Token Scams
Fake crypto token scams are designed to blend into the normal crypto experience, which is why they are often hard to spot at first. From unsolicited airdrops to fake upgrades and misleading swaps, these scams rely on confusion and quick reactions rather than technical complexity. Knowing how fake tokens work and how they enter wallets helps reduce the risk of further loss.
When a fake token scam has already occurred, careful action matters. Securing wallets, preserving transaction details, and understanding the movement of funds can help limit damage. In many cases, reviewing the situation with specialists in crypto scam recovery can help bring clarity around what happened and what recovery paths may still exist. If you have been affected, it is important to contact recovery experts as soon as possible to assess your options.
Even when outcomes are uncertain, informed guidance and timely steps can help victims regain control and avoid repeated exposure to similar scams.
FAQs (Frequently Asked Questions)
A fake crypto token scam involves a token that has no real project, value, or purpose. These tokens are created to trick users into sending crypto, approving malicious transactions, or connecting their wallets to unsafe platforms. Even though the token may appear real in a wallet, it is designed to cause financial loss rather than offer a legitimate investment.
Fake crypto tokens can appear in a wallet because anyone can send a token to any wallet address without permission. Wallets do not verify whether a token is legitimate. Scammers use this method to place fake tokens in wallets and encourage users to interact with them, which can lead to further risks.
No, a fake token cannot steal funds simply by appearing in a wallet. Losses usually happen when a user interacts with the token, such as approving a smart contract, attempting a swap, or connecting to a fake website. Avoiding interaction with unknown tokens helps prevent further damage.
After interacting with a fake token, stop all further activity related to it. Revoke any wallet approvals, move remaining funds to a secure wallet, and save transaction details such as wallet addresses and transaction IDs. Acting quickly can help limit additional losses.
Crypto scam recovery depends on how the scam occurred and where the funds were sent. In some cases, blockchain analysis can trace transactions and identify potential recovery paths. While recovery is not guaranteed, reviewing the situation with crypto scam recovery professionals can help clarify what options may still be available.