- Cryptocurrency
- May 6, 2025
Table of Contents
Imagine waking up to find your entire crypto balance gone with no warning, no trace. That’s the brutal reality of account takeover fraud in 2025. In the world of cryptocurrency, account takeover fraud is becoming a significant concern. This type of fraud happens when someone gains unauthorized access to a user's crypto account, often leading to stolen funds and personal information.
Recent reports indicate a sharp rise in such incidents. For instance, in 2025, North Korean hackers reportedly stole $1.5 billion from the Bybit exchange, marking one of the largest crypto thefts to date. Additionally, private key compromises accounted for a significant portion of stolen crypto in 2024.
The impact of these breaches is very extreme. Victims can lose their entire crypto holdings, and platforms may suffer reputational damage. Moreover, the broader crypto ecosystem faces increased scrutiny and potential regulatory challenges.
To combat this, it's essential to understand the basics of crypto fraud, recognize how unauthorized access occurs, and implement effective prevention strategies. This blog will delve into the nature of account takeover fraud in crypto platforms, its effects, and the measures both users and platforms can take to protect themselves.
What is Account Takeover (ATO) in Crypto?
Ever wondered how someone could steal your crypto without touching your wallet? That’s exactly what happens in an account takeover, also known as ATO.
In simple terms, ATO is when a scammer gets into your crypto account and takes full control, just like that. They use stolen passwords, trick you into giving up codes, or exploit weak security to log in as you. Once they’re in, they can lock you out, drain your funds, and vanish without a trace.
Unlike banks, crypto platforms don’t offer chargebacks or refunds. So if someone steals your login and transfers your funds, they’re gone.
That’s why understanding the meaning of account takeover crypto isn’t just helpful; it’s crucial. Because in crypto, one small mistake can cost you everything.
Why are so many Crypto Users getting scammed in 2025?
Because scammers aren’t breaking in, they’re logging in.
Account takeover (ATO) scams have jumped a lot in the crypto space since 2023, according to some reports. It’s one of the fastest-growing forms of online financial crime this year.
Instead of targeting blockchains directly, hackers are now focusing on you. They steal passwords, clone apps, hijack phone numbers, and take over accounts without you even realizing it.
Here’s why ATO fraud is growing in crypto right now:
- Over 20 billion login credentials were leaked globally by the end of 2024, and many are reused on crypto apps.
- Most of the users still rely on weak or reused passwords, making them easy targets.
- Crypto wallet downloads surged in early 2025, giving scammers more entry points.
- Fake crypto apps are now one of the top delivery methods for ATO attacks.
- No fraud protection. Unlike banks, crypto has no built-in safety if you get hacked.
2025 crypto scams are shifting fast, and account takeovers are leading the charge. They’re quiet, quick, and often go unnoticed until your funds disappear.
How Does an Account Takeover (ATO) Attack Work?
In the world of cryptocurrency, an Account Takeover (ATO) is a critical threat in which cybercriminals access users' accounts illegally to steal digital currencies. Knowledge about the crypto hacking techniques used in such attacks is important to protect your investments.
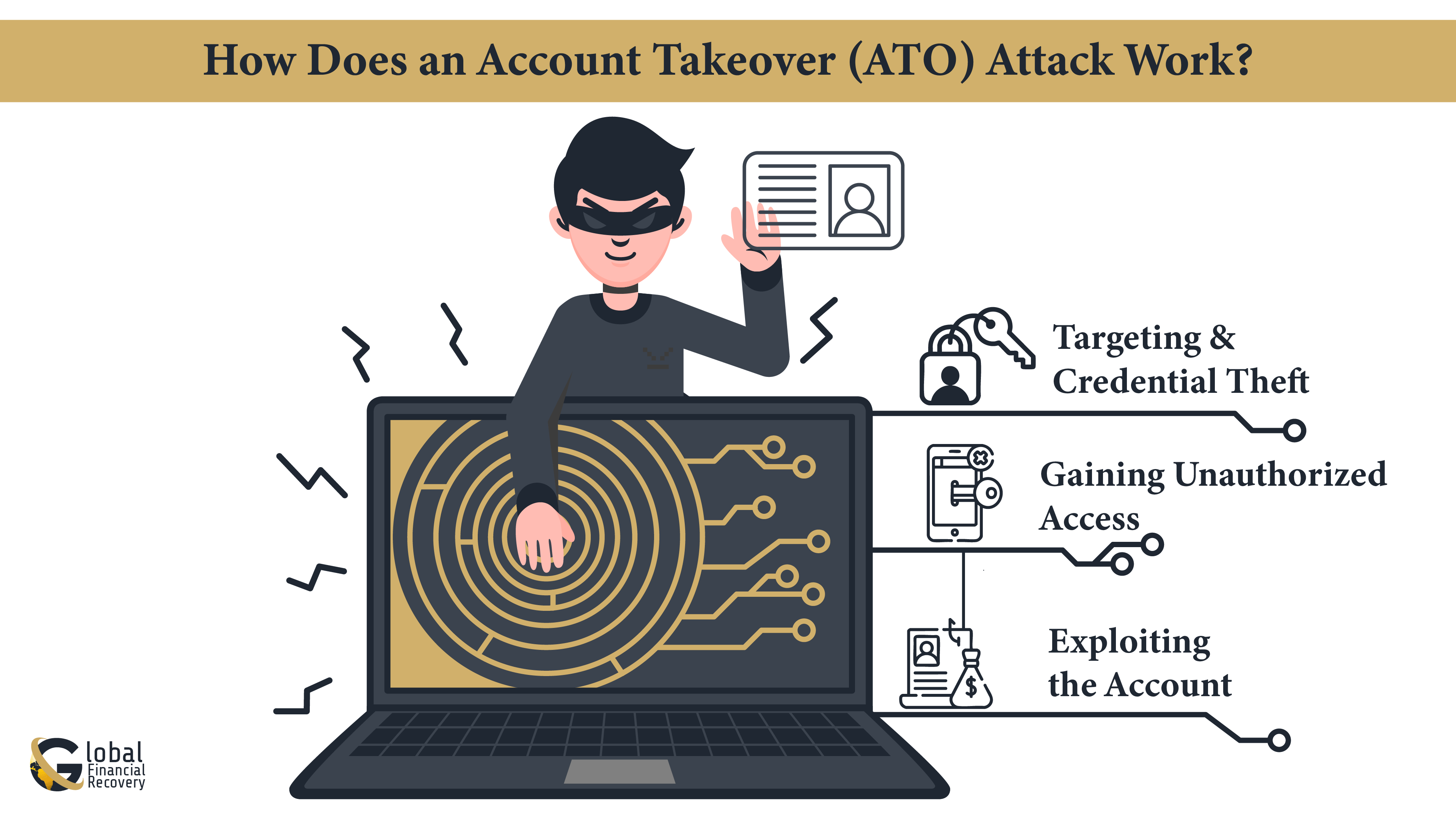
Step 1: Targeting and Credential Theft
Attackers initiate by selecting potential victims, usually targeting users with high crypto balances. They use several methods to acquire login credentials:
- Phishing: Distributing misleading messages or emails that lure users into exposing their passwords and usernames.
- Malware: Contaminating computers with malicious code that records keystrokes or pulls in stored login details.
- Credential Stuffing: Using past-exposed username-password pairs to sign in to accounts, taking advantage of users who use the same password across applications.
These methods are part of the broader spectrum of crypto hacking methods that attackers use to compromise accounts.
Step 2: Gaining Unauthorized Access
With the stolen credentials, attackers log into the victim's crypto account. If two-factor authentication (2FA) is not enabled, or if it's compromised through methods like SIM swapping, the attacker can easily bypass security measures.
Step 3: Exploiting the Account
Once inside, the attacker can:
- Transfer cryptocurrencies to their wallets.
- Change account settings to lock out the rightful owner.
- Use the account for further fraudulent activities, such as laundering stolen funds.
This process illustrates how crypto ATO works, highlighting the vulnerabilities that can be exploited in the absence of robust security measures.
Types of Account Takeover (ATO) Attacks in Crypto
Not all crypto account takeovers happen the same way. Scammers employ various crypto account hacking methods to gain unauthorized access, depending on user habits and the tools they use.
Here are the main ATO attack types in crypto, explained in simple terms:
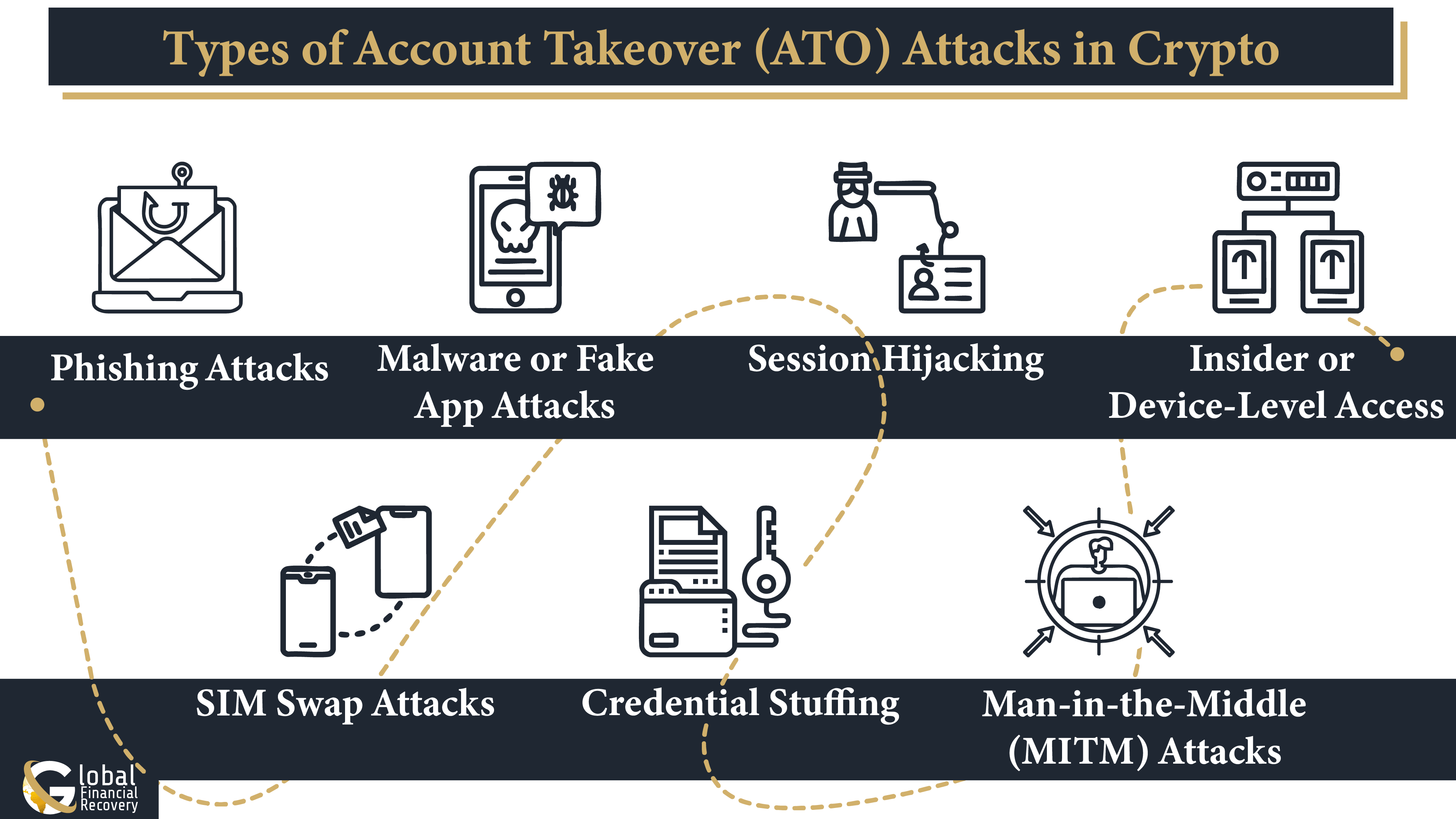
1. Phishing Attacks
There are phishing messages or emails impersonating your exchange or crypto wallet and asking you to log in or resolve something. These direct you to a fake site created to get your credentials. Your attackers can drain your account and take your funds when they acquire these.
Example:
A user gets an email claiming to be from their crypto exchange, announcing that there is suspicious activity on their account. The email directs them to a fake login page. Once they enter their credentials, the attacker controls the user's account.
2. SIM Swap Attacks
Scammers trick your cell provider into porting your phone number to their SIM card. They get your two-factor authentication (2FA) codes and can reset your password and gain access to your account.
Example:
The attacker obtains some personal details about a victim and calls the cell carrier, impersonating the victim. They apply for a SIM swap, and once accepted, they intercept 2FA codes and access the victim's crypto accounts.
3. Malware or Fake App Attacks
You download a fake wallet or browser extension that secretly records your actions or steals login data from your device. The malware operates silently, capturing your seed phrase or session information without your knowledge.
Example:
A user downloads a fake crypto wallet app from an unofficial source. The app contains malware that records keystrokes, capturing the user's private keys and sending them to the attacker.
4. Credential Stuffing
Hackers use email and password combinations leaked from other sites and try them on crypto platforms. This method is effective because many people reuse the same password across multiple websites.
Example:
An attacker obtains a list of leaked credentials from a data breach and uses automated tools to try these combinations on various crypto exchanges. If users have reused passwords, the attacker gains access to their accounts.
5. Session Hijacking
You are logged into a crypto account using public Wi-Fi, and an attacker can steal your session without knowing your password. They can use your account while you're already logged in, even if they do not know your login credentials.
Example:
A customer uses their crypto wallet on a public Wi-Fi network. A hacker using the same network intercepts the session token and can hijack the user's account.
6. Man-in-the-Middle (MITM) Attacks
A hacker secretly intercepts communication between you and a crypto site, particularly on an unsecured connection. They can harvest sensitive information in real-time, even if the site is secure.
Example:
A user uses an unsecured public Wi-Fi to access their crypto exchange. An attacker intercepts the communication, harvesting login credentials and other sensitive information.
7. Insider or Device-Level Access
A trusted individual or malware already on your device accesses your crypto app, logs in, or exports your private keys. This attack often occurs without a trace, exploiting the trust you place in the device or person.
Example:
It is a friend or colleague who installs spyware on your device and monitors your cryptocurrency activities and retrieves private keys along with the login information.
One's knowledge of such methods used to steal one's logins is vital in the protection of one's digital assets. Measures should be put in place in order to close the chances against all these threats, and strong and unique passwords, two-factor authentication, and caution when opening emails or downloading files.
Signs of a Crypto Account Takeover
If you’ve ever felt that something wasn’t quite right with your crypto account, you’re not alone. Account takeover (ATO) attacks don’t always happen loudly. In fact, many victims only realize what’s happened after it's too late.
This section will help you recognize the early signs of a crypto account takeover, so you can take action before further damage is done.
1. Unrecognized Login Attempts
If you are getting notifications on logins from unknown devices or geographies, particularly at strange hours, then it might be a sign of unauthorized access. Tracking login activities assists in the early detection of any malicious activity.
2. Unexpected Account Changes
Sudden changes in your account settings, including email address, phone number, or password, without your action, are warning signs. The changes may be attempts by attackers to freeze you out of your account.
3. Unusual Transactions
Unrecognized transactions, particularly big withdrawals or transfers to unidentified wallets, are good signs of an attacked account. Keeping an eye on your transaction history can help identify such irregularities.
4. Several Failed Login Attempts
Noticing several failed login attempts is indicative that perhaps someone is attempting to break into your account with the wrong credentials. This may be a component of a brute-force attack.
5. Difficulty Accessing Your Account
In case your typical login credentials cease to work and you have made no changes, an intruder may have modified your login details to block your access.
How to Protect Your Crypto Account?
Securing your crypto doesn't have to be difficult. These are the best and simplest steps to remain secure from Account Takeover (ATO) attacks:
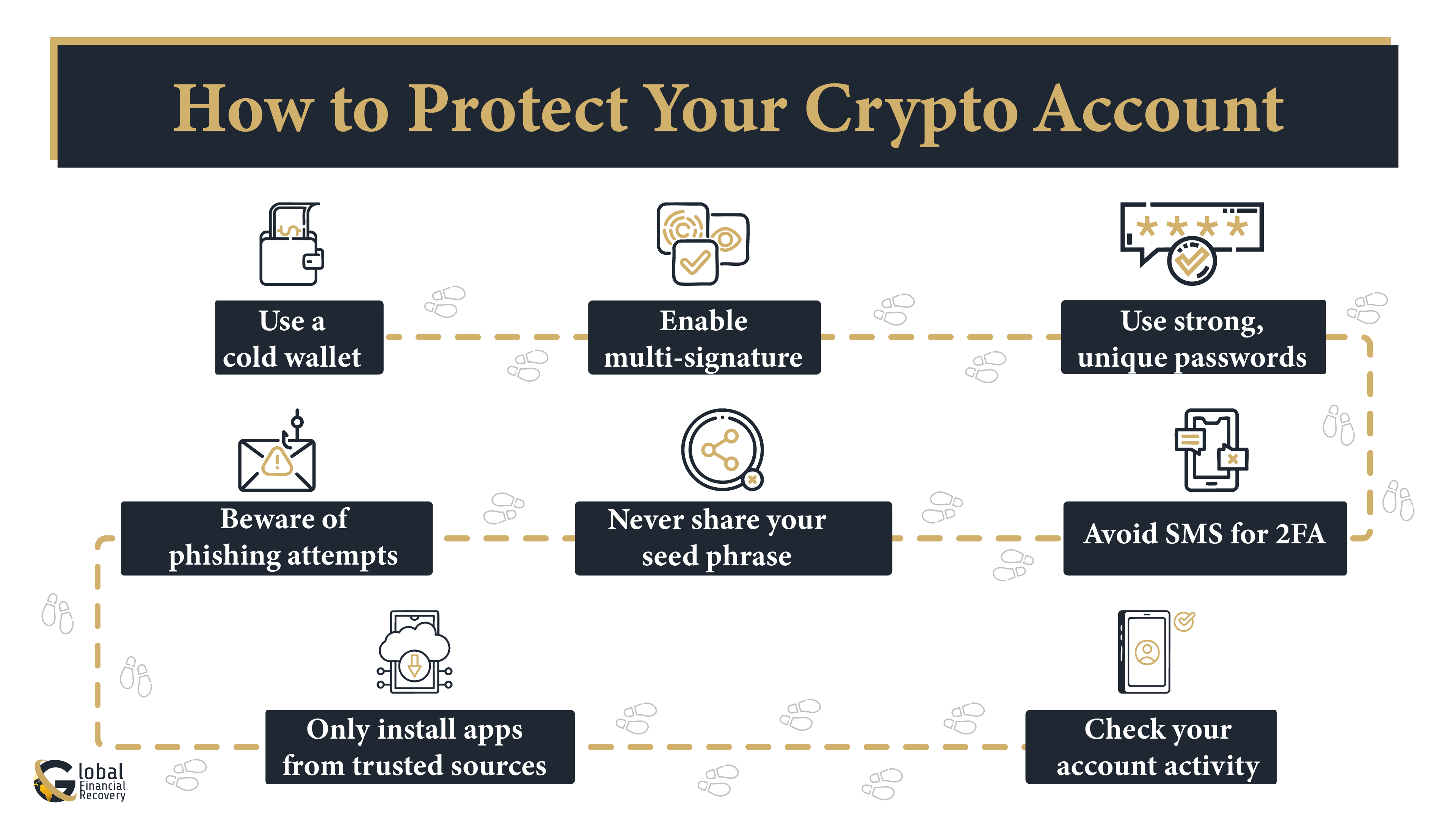
Begin by putting your crypto in a cold wallet. Cold wallets are offline, and hackers cannot get to them via the internet. They are ideal for keeping lots of crypto secure.
For extra protection, use a multi-signature wallet. It takes more than one key to sign off on a transaction. So if someone steals one key, your money is still safe.
Always use strong, unique passwords. Never reuse the same one across multiple platforms.
Skip SMS for two-factor authentication. Use an app like Google Authenticator instead. It’s safer and harder to hijack.
Never share your seed phrase. Don’t store it on your phone or email. Write it down and keep it somewhere safe.
Be careful with emails and messages. Don’t click on random links or attachments, even if they look official. Go directly to your exchange or wallet website.
Avoid downloading unknown crypto apps or tools. Stick to trusted sources like official websites or app stores.
Don’t log into your wallet on public Wi-Fi. Use a VPN if needed, or wait until you’re on a secure connection.
Keep your phone and computer updated. Use antivirus software and remove anything you don’t trust.
Lastly, check your accounts often. If you see anything unusual, act fast.
What to Do Immediately After an Account Takeover Hack?
Discovering that your crypto account has been hacked can be a devastating experience. It’s emotional, overwhelming, and often confusing. But what you do next matters, and it can make a real difference.
If you believe your account has been taken over, here are the critical steps to take right away to increase your chances of recovery:
1. Stop All Activity and Disconnect
If you're still logged in to your wallet or exchange account, log out from all devices. If not, immediately disconnect your device from the internet to prevent further access. This helps stop any ongoing transactions or remote control.
2. Reset All Passwords and Secure Accounts
Change your login credentials on all linked accounts, email, exchange, and even 2FA tools from a secure, uncompromised device. If you suspect malware, reset from a device you trust.
3. Notify the Crypto Platform or Wallet Provider
Immediately report the incident to the platform (like Binance, Coinbase, or MetaMask). Some exchanges may freeze the account to prevent more damage or flag suspicious transactions internally.
4. Document Everything
Take screenshots of:
- Unauthorized transactions
- Email or SMS notifications
- Login alerts
- Support messages
Having a timeline of the events strengthens your case when speaking to platforms or professionals.
5. Contact a Trusted Crypto Recovery Service
Time is crucial. If your funds have already been moved, professional help can trace the wallet addresses, flag them to exchanges, and assist with reporting to authorities. This is where Global Financial Recovery comes in.
Final Words
Account Takeover (ATO) fraud is no longer just a technical problem; it’s a human one. It preys on everyday habits: reusing passwords, clicking on trusted-looking emails, or feeling safe on a device that’s already been compromised.
What most guides won’t tell you is that even simple changes in your behavior can save you from major losses.
Yes, scammers are getting smarter. But so can you.
By following the steps outlined in this article, from using cold wallets and strong passwords to recognizing red flags and knowing who to contact after a hack, you’re already doing more than most users to protect yourself.
And that matters.
Because prevention doesn’t just protect your funds, it protects your peace of mind.
Need Help Recovering Stolen Crypto?
FAQs (Frequently Asked Questions)
A "Dead Man’s Switch" in cryptocurrency refers to a mechanism that automatically transfers access to your crypto assets to a designated party if you become inactive for a specified period. This ensures that your assets are not lost due to unforeseen circumstances.
Proof of personhood is a method for validating that every participant in a network is a unique human being. Such a mechanism serves to prevent Sybil attacks, in which a single entity generates multiple fake identities to gain undue influence, by insisting on user uniqueness, thereby providing an additional measure of security against account takeover.
Yes, cybercriminals now use AI generated deepfakes meant to impersonate someone trusted or any celebrity in order to promote fraudulent crypto schemes. These seem so real that they can mislead a user into investing in a scam, causing account takeovers and massive financial losses.
Instead of deceiving users into logging in at some fake site, attackers now just ask the user straight up for a recovery phrase via fake pop-ups, wallet errors, or impersonating someone from support. In doing so, they skip around any other security and gain immediate access to funds.
Yes. If someone with device access unknowingly installs malicious apps, accepts suspicious links, or shares login details, it can lead to an unintentional ATO. Educating anyone with access to your device is crucial.