- Cryptocurrency
- October 29, 2024
Table of Contents
Imposter scams in crypto have damaged investor confidence across the board. Fraudsters will copy trusted influencers, make fake support accounts, and create convincing rip-offs of the real platforms for their crimes. It’s not just about the money; many victims end up losing trust in the entire crypto world.
This article breaks down the tactics that impostors rely on, showing you what to look for before trouble starts, and explains how to keep your crypto safe. We'll also cover your next steps if you've already been targeted and fund recovery.
What Are the Crypto Impostor Scams?
Crypto impostor scams involve criminals pretending to be credible individuals in the cryptocurrency industry. They might fake an influencer's profile, pose as project support staff, or copy a legitimate exchange's website. The end goal is always to mislead you into sending funds, revealing private keys, or clicking on malicious links.
Unlike pump-and-dump scams or rug pulls, impostors, specifically fake accounts, are based on borrowed credibility. Scammers do not create something new; they use an existing reputation. This makes them especially dangerous because everything looks authentic until you've already lost money.
Common Platforms for Imposter Scams
- Social Media – Fake profiles on Twitter/X and Instagram running phony giveaways
- Chat Platforms – Imposters in Telegram and Discord posing as moderators or admins
- Email/DMs – Phishing messages disguised as security alerts or support tickets
- Fake Websites – Nearly perfect copies of real exchanges designed to capture login details
How the Imposter Scam Works?
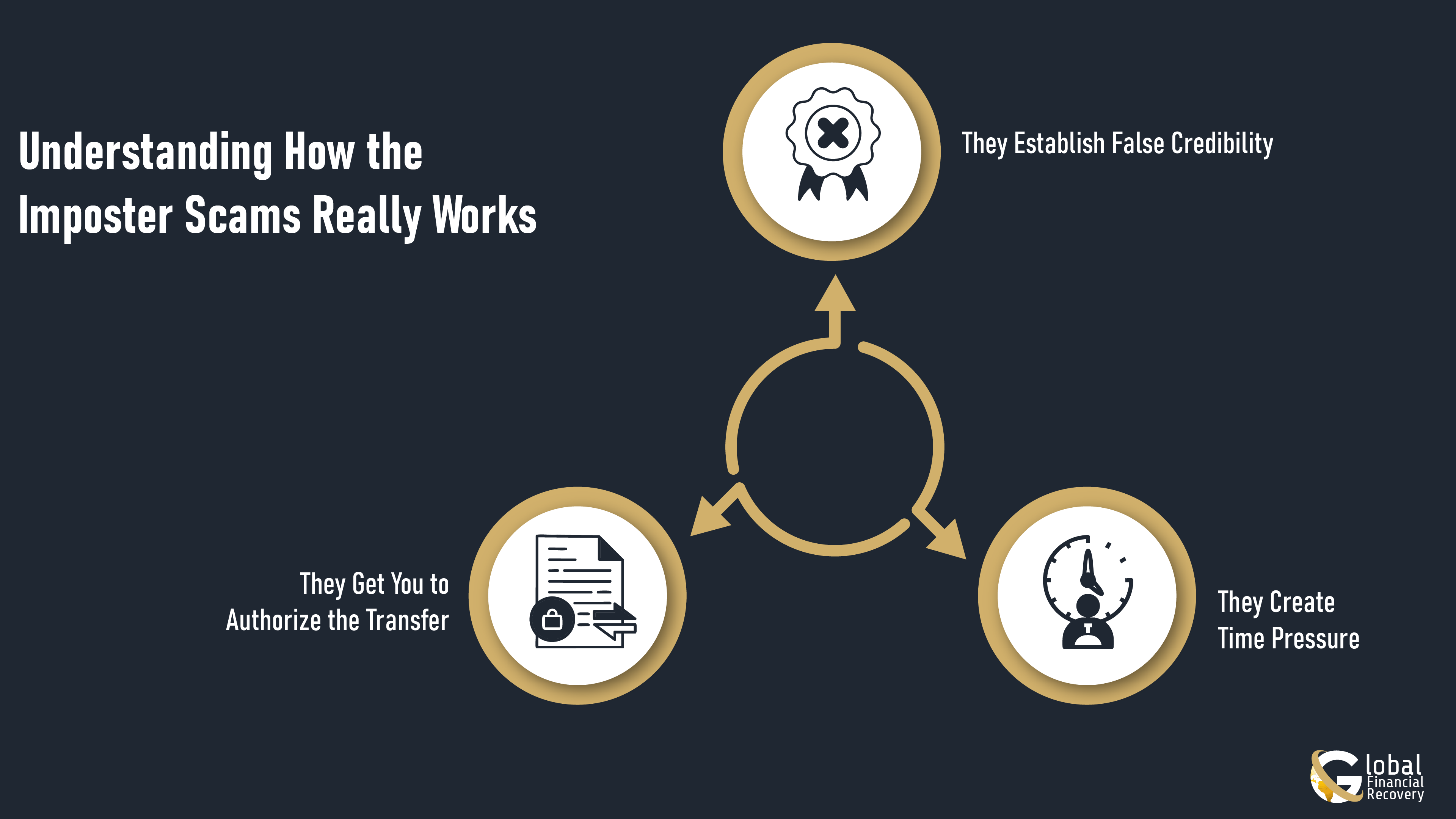
These scams work because they feel legitimate and personalized. Here's how they usually play out:
-
They Establish False Credibility
Imposters start by copying someone trustworthy. You might receive a message from what appears to be a known crypto expert, or visit a website that looks exactly like your regular exchange, except for one letter in the URL. By seeming credible from the start, they get past your initial skepticism.
-
They Create Time Pressure
Once you're engaged, they push urgency. Limited-time offers, account security warnings, or exclusive opportunities that expire soon are all designed to make you act on emotion rather than logic. The pressure is the point.
-
They Get You to Authorize the Transfer
Finally, they convince you to send crypto yourself. They'll provide a wallet address with a plausible reason why you need to send funds first. You're not being hacked, technically; you're approving the transaction. Once sent, the crypto is gone.
Recognizing this pattern helps you spot problems before they become losses. Now, let's look at some of the types of imposter scams to better understand and safeguard yourself.
Different Types of Imposter Scams You Should Know
Crypto impostors use different tricks to look real and win your trust. Here are the most common types of impersonation scams and how they usually work:
|
Scam Type |
How It Works |
Examples |
|
Scammers copy the names, photos, or profiles of famous people to promote fake giveaways or “guaranteed” investments. |
A fake Elon Musk Twitter/X account promising to double your Bitcoin if you send some first. |
|
|
Fraudsters build trust through online relationships, then steer victims toward fake crypto platforms. |
A person you meet on Telegram or dating apps who slowly convinces you to “invest together” in a secret crypto deal. |
|
|
Company or Government Impersonation |
Scammers pose as banks, exchanges, or tax authorities to pressure you into urgent crypto payments. |
An email saying your Binance account will be frozen unless you transfer USDT; a fake IRS caller demanding Bitcoin for “back taxes.” |
|
Fake Customer Support |
Imposters act as official exchange or wallet staff to trick you into sharing sensitive details or paying fake “fees.” |
A fake Coinbase support agent on Telegram is asking for your seed phrase to “unlock” your account. |
|
Fake Websites & Apps |
Lookalike platforms steal login details, seed phrases, or directly drain wallets. |
A phishing site like coinbaase.com, a fake wallet app on the Play Store that requests private keys. |
|
Victims are lured by offers of free tokens or doubled returns if they send crypto first. |
A YouTube stream offering “Send 1 ETH, get 2 ETH back.” |
|
|
Community & Admin Impersonation |
Scammers infiltrate Telegram/Discord groups, pretending to be admins or project founders. |
A “project admin” sends you a personal message to fix wallet issues and asks for your private key. |
|
Malicious links disguised as account alerts or rewards trick users into revealing info. |
An email urging you to “verify your wallet” through a fake link. |
|
|
Posing as recruiters or traders, scammers promise high returns if you invest or deposit upfront. |
A job ad that requires USDT deposits for “training”; a “trader” guaranteeing 20% daily profit. |
|
|
Fraudsters claim they can recover stolen funds but only demand fees without results. |
A recovery website promising to trace your lost ETH for a hefty advance payment. |
These are the most common ways impostors try to trick you. Knowing the types helps you stay alert, and next, we’ll go over how we can spot imposter scams.
Key Warning Signs of Imposter Scams

Spotting imposter scams early can save you serious money and stress. Watch for these red flags:
-
Profiles That Don't Quite Match
Imposters duplicate legitimate accounts but with subtle differences, such as a slightly altered username, a newer account with similar branding, or copied content. Checking account age, verification status, and engagement patterns reveals most impostors.
-
Urgent Demands for Action
"Act now or lose this opportunity," and "Your account will be locked unless you respond immediately" are classic manipulation tactics. Legitimate services give you time to think. When someone needs an instant decision, that's usually a problem.
-
Asking for Private Keys
This is the clearest red flag. No legitimate crypto service, exchange, or support team will ever request your private keys or seed phrase. Anyone asking for this information is an imposter attempting theft; no legitimate exceptions exist.
-
Strange Links or Connection Requests
Always examine URLs before clicking. Imposters create nearly identical websites with tiny spelling differences. Any unexpected request to connect your wallet or visit a link should trigger verification steps.
-
Unrealistic Promises
Risk-free returns, guaranteed profits, or instant doubling of your crypto are virtually always scams. Real investing involves risk, and anyone claiming otherwise is an imposter.
These signs make it easier to spot scams before they cost you. Let’s now focus on how to protect your crypto from impostors.
Case Study: Fake Binance Support Impersonators
Scammers set up Telegram profiles that looked identical to Binance’s official support team. These impostors told users their wallets had “security issues” and asked for seed phrases to restore access.
Victims lost their crypto instantly. The scam also weakened trust in real Binance staff, making it harder for users to know who’s genuine.
Protecting Your Crypto From Imposters

Building strong security habits matters more than any single action:
- Verify Everything
Check URLs character by character. Only follow officially verified accounts. When uncertain, navigate directly to the official website instead of clicking links. - Ignore Urgency
Real opportunities don't disappear because you took time to research. Imposters use pressure because research exposes them. Always pause before acting. - Keep Keys Private
Your seed phrase and private keys should never be shared with anyone, ever. They're equivalent to handing over complete access to your accounts. - Check All Links
Before connecting your wallet anywhere, verify the exact URL. Only download apps from official app stores. Be extra cautious with links in messages. - Stay Updated
Imposter methods evolve constantly. Following crypto security communities and news helps you recognize emerging threats.
By staying careful and verifying everything, you can avoid most scams. Next, we’ll go through what to do if you find yourself a victim.
Steps After Being Targeted by an Imposter
Discovering you've been targeted is tough, but quick action helps:
- Save All Evidence: Screenshot everything: messages, transactions, wallet addresses, emails, and timestamps
- Report Immediately: Contact the platform where the scam occurred and file reports with cybercrime authorities
- Remove Permissions: Use Revoke. Cash or Etherscan to cancel any suspicious wallet approvals
- Warn Others: Share details in crypto communities to prevent additional victims
- Consider Recovery Services: For major loss, check for legit crypto recovery services that help you get your money back.
- Strengthen Security: Change the passwords, enable two-factor authentication, and move to secure wallets with the remaining funds.
The Smart Way to Stay Safe in Crypto
Protecting yourself in crypto comes down to verification and skepticism. When offers seem too generous or someone's rushing you, those are warning signs, not opportunities.
Your crypto security depends primarily on your own awareness. Put simply, you considerably lessen your risk by checking sources, protecting private information, and then verifying before acting on them. Something that does not sit well with you probably never should have.
If you’ve been scammed or need guidance, don’t wait, contact Global Financial Recovery and our team will guide you step by step.
FAQs (Frequently Asked Questions)
They often begin with a message, email, or post from a profile that looks like a trusted influencer, project, or exchange. The scammer builds trust quickly and then asks for money, private keys, or directs you to a fake website.
Yes. These scams are designed to look convincing, even for people who know the crypto space well. Because they rely on trust and social proof, they can fool beginners and experienced investors alike.
A phishing attack usually involves fake websites or links that steal your login details. An imposter scam focuses on social engineering. The scammer pretends to be someone you trust, like a project admin or influencer, to get you to send funds directly.
Look closely. Is the username slightly off? Are they pushing you to act fast? Do they promise guaranteed returns? Real projects don’t ask for your private keys or rush you into decisions. When in doubt, check the official website or verified accounts directly.
Yes. Many impersonators run “giveaway scams,” where they claim you’ll get free tokens if you send some first. Since the message comes from a profile that looks real, people fall for it, but once you send crypto, it’s gone.