- Cryptocurrency
- March 31, 2025
Table of Contents
In recent years, cryptocurrency has steadily gained popularity. As the crypto market has been viewed as an alternate source of income, securing your cryptos has become essential. But with so many wallets available in the market nowadays, how do you know which one will protect your precious investment? The wrong choice could put your funds at risk, leaving you vulnerable to theft or loss.
Thus, with several options available online for safely securing your cryptos, choosing the best crypto wallet is important. In this article, we will take a deep dive and provide you with options to choose from several crypto wallets available in the market.
Why Does Choosing the Right Crypto Wallet Matter?
Digital assets are easy targets for scammers and hackers, and the crypto market is frequently subjected to cyber threats. Losing your crypto holdings to scammers can be financially and mentally devastating. Thus, you need to select one of the best crypto wallets.

Risks Involved Choosing a Wrong Crypto Wallet
Cryptocurrencies are digital assets; the crypto market is highly lucrative and volatile. One of the advantages of cryptocurrency is that the transactions are immutable or cannot be reversed as they get recorded on the blockchain network as a ledger. However, this advantage is also its disadvantage, as recovering these cryptos requires special software and hardware.
Scammers are frequently targeting their potential victims and try to siphon off their cryptos through social engineering, security breaches, phishing, fake wallets, and so forth.
Importance of Self-Custody & Secure Storage
When you trade in the crypto market, it is important to understand who controls the ownership of your cryptos. A secure and self-custody crypto wallet offers complete ownership of your crypto holding, allowing you to trade as and when you wish. Thus, besides you, no one can have access to your private keys since you have complete ownership.
Choosing the best crypto wallet will offer the best cyber security against potential cyber threats and help secure your private keys.
Types of Crypto Wallets & Their Security Levels
There are several types of crypto wallets available online, and each type differs in ease of accessibility and security. The choice is yours depending upon your need and how often you trade in the crypto market.
There are mainly three types of crypto wallets, and they are as follows:
- Hot Wallet: These are best for those crypto users who frequently access the crypto market. Crypto users store their tokens and cryptos on an online crypto wallet provider.
- Cold Wallet: These are best for those crypto users who do not trade in the crypto market frequently. They are like hardware and can be connected to the internet during transactions, thus the name cold wallet.
- Multi-Sig & MPC Wallets: Multi-Sig crypto wallets require multiple parties or signatures to access the cryptos. MPC, or Multi-Party Computation crypto wallets, splits private keys into multiple shares; thus, no single entity has full control.
Tabular representation of: Overview of All Crypto Wallet Types
|
Wallet Type |
Security Level |
Best For |
Key Features |
Examples |
|
Hot Wallets |
Medium |
Frequent transactions and trading |
Connected to the internet, fast, easy to use, vulnerable to online attacks |
MetaMask, Trust Wallet, Exodus |
|
Cold Wallets |
High |
Long-term storage and security |
Offline, highly secure, great for holding assets over time without risking hacking |
Ledger Nano X, Trezor Model T |
|
Hardware Wallets |
Very High |
Storing large amounts of crypto |
Physical devices, private keys stored offline, resistant to malware |
Ledger Nano S, Trezor One |
|
Paper Wallets |
Very High |
Maximum security for long-term storage |
Printed or written keys, completely offline, vulnerable if lost or damaged |
Paper wallet generators, custom-printed wallets |
|
Web Wallets |
Low to Medium |
Quick access to funds and multi-device use |
Accessed through browsers, convenient but vulnerable to phishing and hacking |
Blockchain Wallet, Coinbase Wallet |
|
Mobile Wallets |
Medium |
On-the-go transactions, mobile app-based |
Installed on smartphones, easy to use, can be hacked if the phone is compromised |
Trust Wallet, Mycelium |
|
Desktop Wallets |
Medium to High |
Security and control of personal computers |
Installed on desktops, more secure than web wallets, requires securing your computer |
Electrum, Exodus, Armory |
|
Custodial Wallets |
Low to Medium |
Beginners and traders who prefer convenience |
Managed by third parties (exchanges), less control but easier to use |
Coinbase, Binance Wallet |
|
Non-Custodial Wallets |
High |
Full control over assets and privacy |
You control your private keys, offering greater security but requiring more responsibility |
Electrum, Exodus, Mycelium |
|
Multi-Signature Wallets |
Very High |
Businesses, high-transaction environments |
Requires multiple signatures to authorize a transaction, adds extra security layers |
Casa, Gnosis Safe |
|
MPC (Multi-Party Computation) Wallet |
Very High |
Institutions, enterprises, and high-net-worth individuals |
Keyless security, threshold signing, off-chain approval |
Fireblocks, ZenGo, Coinbase WaaS |
Factors to Consider When Choosing a Crypto Wallet
Several factors are critical while choosing the right wallet; they are as follows:
- Private Key Control & Non-Custodial Security – Ensures users have full ownership and control over their private keys, reducing reliance on third-party custodians.
- Multi-Factor Authentication (MFA) – Adds an extra layer of security, requiring multiple verification steps to access funds and prevent unauthorized transactions.
- Backup & Recovery Options – Provides secure seed phrases or encrypted backup solutions to restore access in case of device loss or failure.
- Compatibility with DeFi & NFTs – Supports seamless interaction with decentralized finance (DeFi) protocols and non-fungible tokens (NFTs) for asset management and trading.
- User-Friendly Interface – Intuitive design for easy navigation, transaction management, and portfolio tracking.
- Cross-Platform Accessibility – Availability on multiple devices (mobile, desktop, browser extensions) for convenient access to crypto assets.
- Hardware Wallet Integration – Supports cold storage options for enhanced security against cyber threats.
- Multi-Asset Support – Allows storage and management of various cryptocurrencies and tokens in a single wallet.
- Open-Source & Audited Code – Transparent and regularly reviewed codebase to ensure security and trustworthiness.
- Low Transaction Fees & Customization – Offers flexible fee structures and the ability to adjust gas fees based on network congestion.
Common Crypto Wallet Security Risks
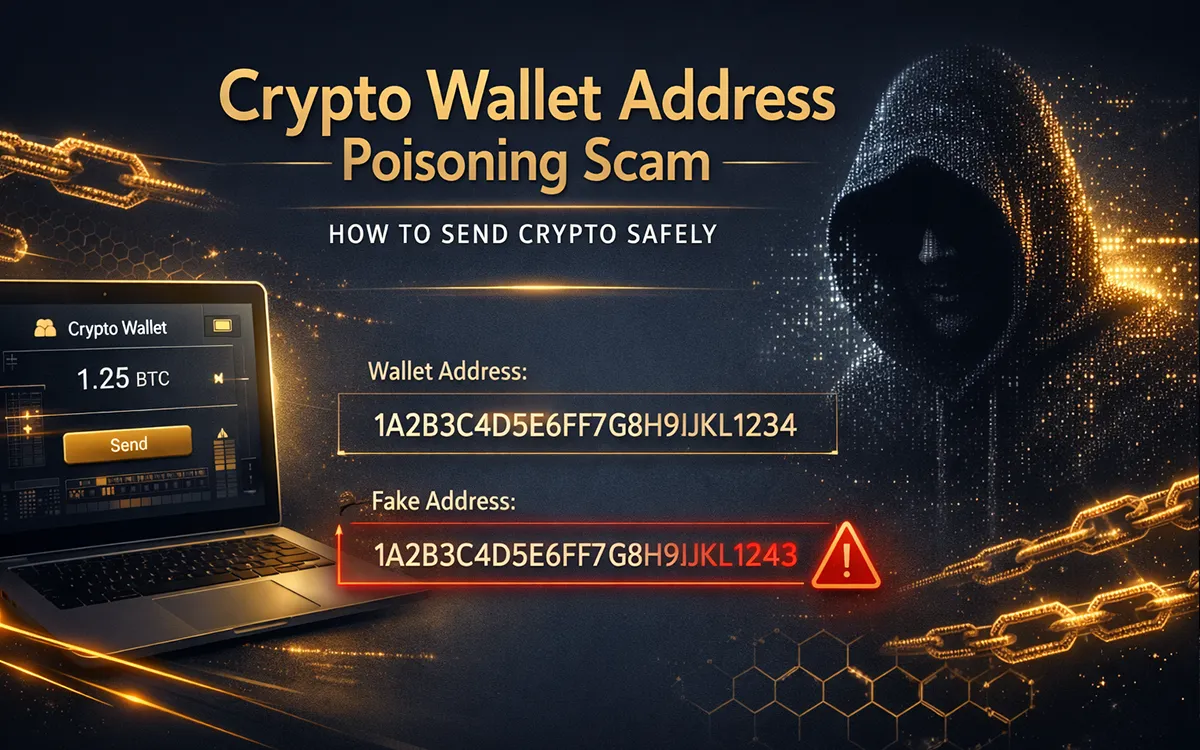
Crypto wallet risks include fake wallet scams, where malicious apps steal funds, and phishing attacks that trick users into revealing private keys. Crypto fraud prevention involves using trusted wallets, enabling two-factor authentication, and verifying official sources before downloading apps. Always store private keys securely to protect your assets from cyber threats.
"Many fraudulent wallets pose as legitimate options. Learn how to spot and avoid them in our in-depth article on Fake Crypto Wallet Scams."
- Beware of fake crypto wallets: Malicious apps are stealing private keys, putting your funds at risk!
- Phishing attacks: Crypto users face phishing attacks through fake wallet websites, risking fund theft when selecting fraudulent crypto wallets.
- Rug pulls & exit scams in wallet-based DeFi projects: Crypto users risk rug pulls and exit scams in wallet-based DeFi projects, often falling for fake wallets that drain their funds.
Beginner’s Checklist: How to Choose a Secure Crypto Wallet
Choosing the correct crypto wallet is of utmost importance for safe storage and seamless transactions. Below is a quick checklist on how to pick the best option:
- Private Key Access: Establish jurisdiction over private keys to wholly control funds.
- Security Audits: See if the application has been subjected to a security audit by reputable companies in order to avoid vulnerabilities.
- Fake Wallet Risks: Beware of apps posing as cryptocurrency wallets and download them only from verified sources to prevent scam recreations.
Concentrating on crypto wallets will improve the security of crypto storage, making a devoted selection pattern on how to select a crypto wallet that suits personal needs.
Best Practices for Storing Crypto Securely
To prevent crypto theft, avoid phishing scams and never share sensitive information. Thus, follow these steps to store crypto safely and protect your investments.
- Use Cold storage vs. Hot storage: Use cold storage for long-term holding and maximum security (offline hardware wallets). Use hot storage for quick access and frequent transactions (online wallets), but be mindful of security risks.
- Enhance Security with Multi-Signature & Hardware Wallets: Enhance your crypto security with multi-signature wallets for shared control and hardware wallets for offline protection—keeping your assets safe from hacks and theft.
- Avoid browser extensions: Avoid browser extensions for crypto wallets to avoid phishing risks—opt for hardware or mobile wallets for secure transactions. Use them when making transfers or storing assets long-term.
Key Takeaways
In this article, we have mentioned the importance of choosing the right crypto wallet and distinguishing between a genuine one and a fake one.
- Choose a Secure Wallet – Opt for hardware wallets like Ledger or Trezor for maximum security.
- Enable Two-Factor Authentication (2FA) – Adds an extra protection layer.
- Use Strong Passwords & Backup Phrases – Store them securely offline.
- Avoid Phishing Scams – Never share private keys.
- Regularly Update Wallet Software – Patches vulnerabilities.
Recommended Wallets: Ledger Nano X, Trezor Model T, MetaMask (for convenience), and Trust Wallet.
By following these best practices, you can protect your crypto assets from hacks and theft!
FAQs (Frequently Asked Questions)
Exchanges are favorite targets for hackers due to the huge volumes of assets they carry. There have been cases where exchanges lost a lot of funds because of security issues. For instance, in February 2025, Bybit, the world's largest crypto exchange, was hacked, and $1.5 billion in Ethereum was stolen. When you store your crypto on an exchange, you are reliant on the platform's security measures, which may not always be foolproof.
Personal wallets provide stronger protection but at the cost of responsible management. When you lose private keys or recovery phrases, your access to money can be lost forever. Also, hardware wallets can break or get damaged physically, and unless you have secure backups, the recovery will prove difficult. Customers also need to be wary of phishing attacks and make sure that they are actually dealing with the correct wallet interfaces.
It can be useful for frequent traders who need easy access to trading functionality and liquidity. Exchanges tend to have easy-to-use interfaces and other services such as staking or lending. However, for long-term storage or large holdings, moving assets to a private wallet is usually advisable to avoid the security risks of centralized platforms.
For the long-term, storing them in a non-custodial cold hardware wallet is best. Such wallets are offline and therefore safe from theft via internet attacks.
The amount of cryptocurrency within your wallet will not change over time; however, its value can go up or down according to the current market situation.