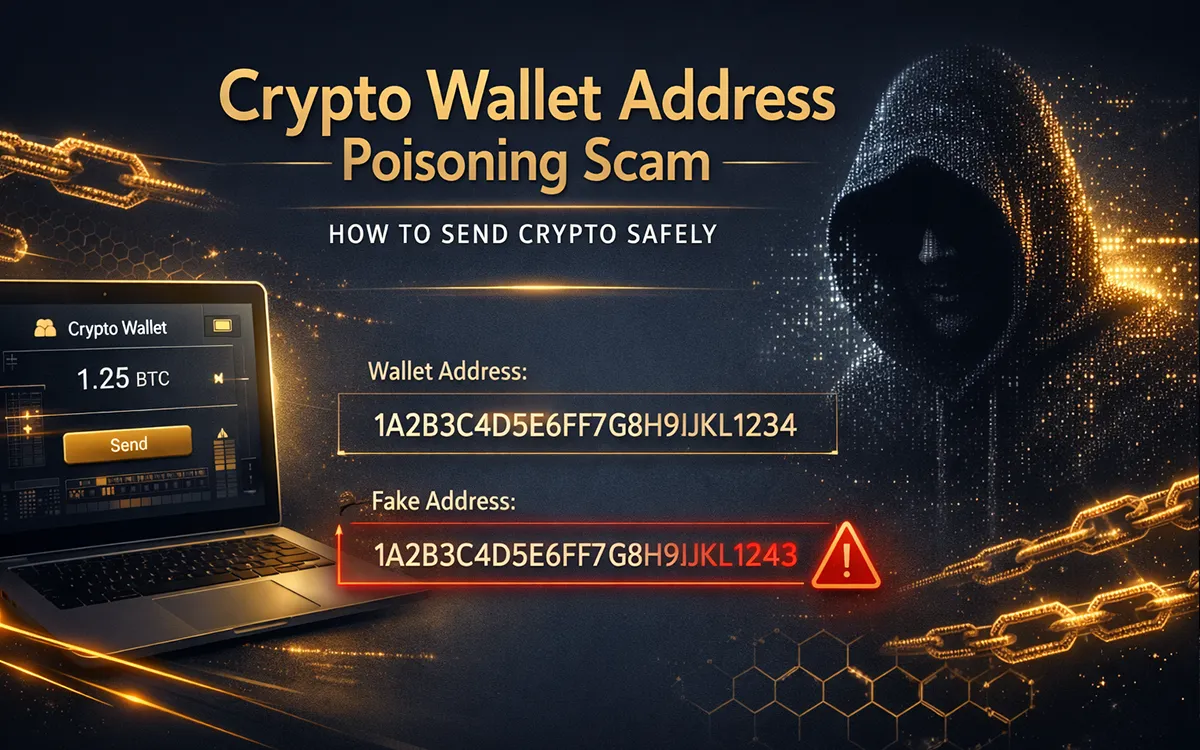
- Social Media
- December 11, 2025
Table of Contents
Social engineering scams are getting smarter. Scammers use emotions to trick you into doing things you normally wouldn’t. They break your faith instead of breaking your computer. They apply emotion, urgency, fear, and confidence tricks to get you to click, send, or share something you would not have otherwise.
The problem has grown even worse now that AI is involved. Fraudsters can now sound natural with AI-generated texts and deepfakes. They send fake bank alerts and even clone social media accounts. Everything is designed to fool you, down to the smallest detail.
It’s no surprise that online banking users, crypto holders, and even casual WhatsApp or Instagram users are getting pulled in. And the harm isn’t only about money. It reaches into other parts of your life, too. Lots of victims report that they felt ashamed, nervous, or had problems sleeping, and asked themselves how a stranger could have easily won their trust.
This guide will take you through the entire process of how social engineering operates, the psychology of social engineering, warning signs to be on the lookout for, and what you can do to be safe. Let's first learn. So, what exactly is social engineering, and why is it so effective?
What Is Social Engineering?
Social engineering is a scam technique that relies on manipulating people, rather than computers. Instead of trying to break into your system, scammers try to influence your choices. That’s what makes it so dangerous; you don’t realize what’s happening until it’s too late.
In simple terms, social engineering is when someone uses emotions and psychology to get you to act. They might pretend to help, create panic, or earn your trust just long enough to make you click, send, or share something you never would have on a normal day.
The most common triggers they use are
- Fear: “Your account will be blocked.”
- Excitement: “You’ve won a reward.”
- Trust: “I’m calling from your bank.”
And because emotions overpower logic, victims act quickly without checking.
You see examples of this every day:
- A phishing email asking you to “update your password.”
- A fake bank call claiming suspicious activity.
- A friendly stranger online is slowly “grooming” you into a crypto investment.
If someone can influence your emotions, they can influence your actions. That’s the core of social engineering. Once scammers understand human emotions, they follow a predictable scam lifecycle designed to break trust step-by-step.
How Social Engineering Scams Really Work?
Social engineering isn’t random. Scammers follow a predictable system, a scam lifecycle designed to lower your guard step by step. When you understand the steps, it becomes easier to stop them early.
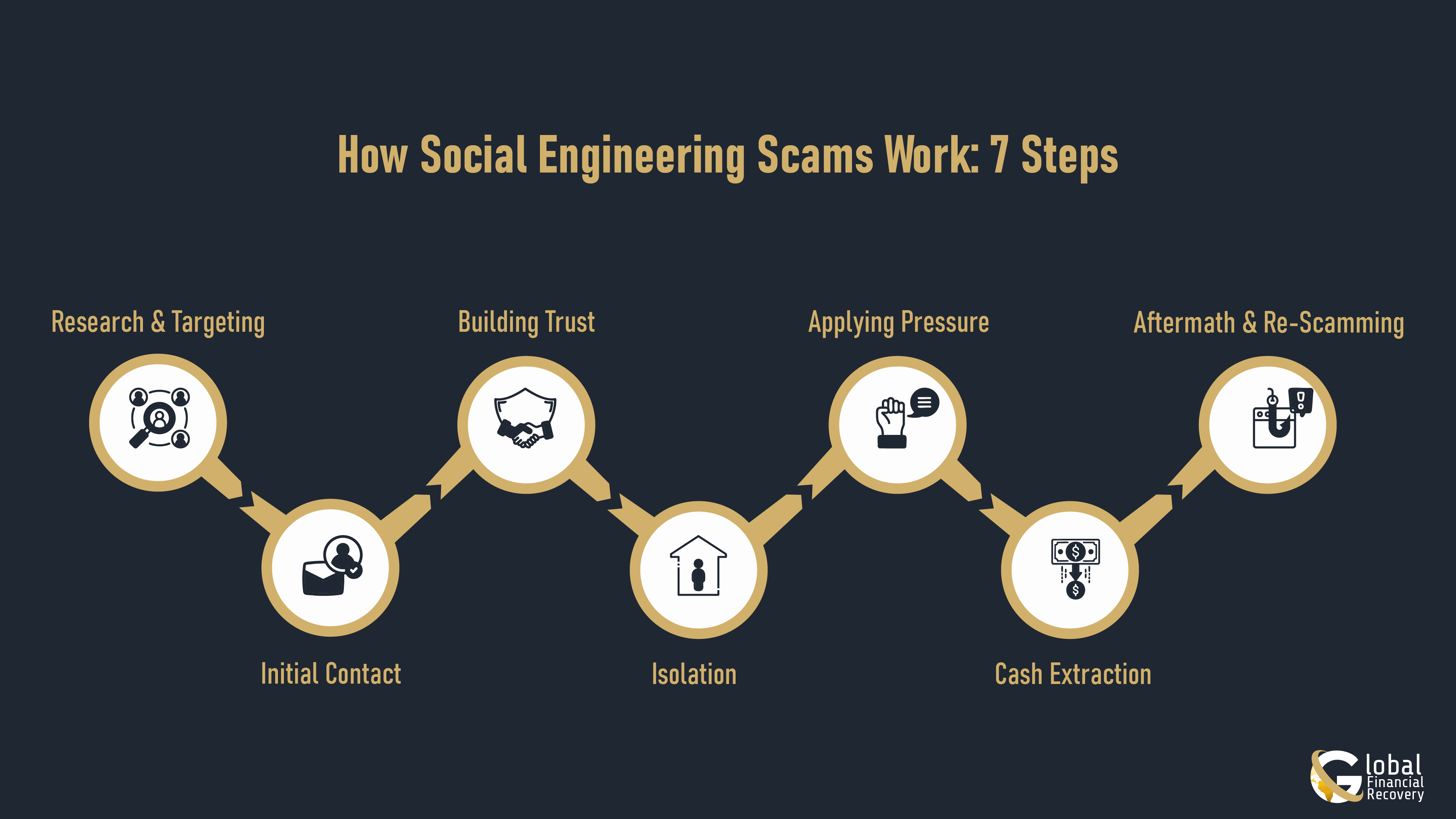
1. Research & Targeting
Every scam starts with research. Fraudsters scan your posts, LinkedIn feed, dating profiles, group chats, and anything that can tell them what you are interested in, your state of stress, your habits at work, or your financial position. The better they know, the less unnatural their approach is.
2. First Contact
Then comes the opening message: a friendly text, a wrong-number text, a cold call, or even a fake job offer. All they need is one reply.
3. Trust Building
Once you respond, the real work starts. They mirror your emotions, share fake stories, act supportive, and build rapport. Some pretend to be bank staff; others act like a friend or romantic partner. Consistency builds comfort.
4. Isolating You
After trust comes isolation. They’ll suggest moving the conversation to WhatsApp or Telegram, saying that it’s “for privacy.” They might even warn you not to tell anyone, framing it as security, not secrecy.
5. The Pressure Phase
This is where the tone shifts. Suddenly, there’s urgency: a time-limited investment, a fake security alert, an account “at risk.” When you’re stressed, you don’t think clearly, and scammers rely on that.
6. Cash Extraction
Once you’re emotionally invested, that's when they attack. They’ll push for a bank transfer, crypto deposit, gift cards, or a peer-to-peer app. Everything feels urgent and necessary.
7. Aftermath
After the money leaves, the scammer changes again. They may disappear, threaten you, or even return pretending to be a “recovery agent.” This is the final twist: re-scamming the victim.
Understanding this cycle is one of the strongest forms of protection. These attacks differ in method but share one goal: convincing you to act without thinking.
Common Types of Social Engineering Attacks and How They Work
Social engineering scams come in many forms, but they all share one thing in common - they rely on tricking people rather than hacking computers. Here are some of the most common types of attacks.

1. Phishing
Phishing refers to the act of fraudsters claiming to be a person you trust (such as your bank or the online store) and deceiving you into providing personal information or clicking on harmful links.
- Spear Phishing: This is a more specific form of the scam in which the attacker targets individuals, such as employees or executives.
- Whaling: Intended as a high-profile attack, such as on CEOs, to steal masses of money or sensitive information.
- Mass Phishing: The email is sent to a large number of people, normally in the form of a generic message about winning something or receiving a fake warning.
These attacks can take many forms, and understanding the different tactics is key to staying safe. For examples of real-world scams and tips on how to recognize them, check out our comprehensive guide on email phishing scams, which covers strategies scammers use across multiple types of phishing attacks.
2. Smishing (SMS Phishing)
Just like phishing, smishing occurs via text messages. Worse, scammers will send you a bogus SMS containing a link or requests for personal information.
Example: Alert text purports something suspicious on your account and requests that you make sure your information is validated by clicking a link.
3. Vishing (Voice Phishing)
Vishing occurs via the telephone. A scammer may call you and introduce himself as your bank or a government agency and attempt to steal your personal or financial information.
Example: This is a call by the customer service requesting that they verify your bank account information.
4. Business Email Compromise (BEC)
In BEC, the fraudsters steal or change an email account belonging to a person in a high rank (such as an executive) to solicit value-added items, such as wire transfers or confidential documents. The fact that BEC does not depend on the malicious links or attachments is what makes it scary: it is all about persuading you to take a risk.
5. Pretexting
It is at this stage that scammers invent an artifice (or pretext) to earn your confidence. They may pretend to be an information technology specialist, a police officer, or even a tax collection agency to lure you into releasing the information.
Example: A fraudster calls, claiming to represent the IT support, and requests that you provide your logins to fix an issue.
6. Baiting
Baiting is the act of giving something enticing (such as free software or a prize) in return for personal information or in order to trick you into downloading malware.
- Physical Baiting: The scammers may even drop an infected USB drive at a gathering area and hope that somebody will insert it into his or her computer.
7. Quid Pro Quo
This is when a scammer offers a service or benefit in exchange for something, your personal info, or access.
Example: An “IT support technician” offering to fix your computer but asking for your login details first.
8. Tailgating/Piggybacking
A physical attack, tailgating happens when someone follows an authorized person into a secure area. They often rely on your politeness, asking you to hold the door because they “forgot their badge.”
9. Honey Trap
This is when a scammer builds a personal relationship (often romantic) to gain your trust and later exploits that relationship to get your personal or financial info.
Example: A person you’ve met online starts asking for money or a crypto investment, saying they “need help.”
10. Dumpster Diving
This might sound old-fashioned, but it’s still effective. Dumpster diving is when attackers go through your trash to find documents with sensitive information they can use to target you later.
Example: Finding old bank statements or account numbers in discarded documents.
11. Watering Hole Attack
This form of attack is based on the aspect of attacking a certain group by hacking into a site that the group uses regularly. As soon as the location is infected, users are deceived into installing malicious content since the site appears to be trusted.
12. Impersonation
Impersonation occurs when an attacker poses as someone you trust, such as a workmate, supervisor, or IT personnel, to gain access to sensitive information.
Example: A scammer claiming to be your boss requests a wire transfer or a confidential document.
Impersonation scams can take many forms and target different victims.For more examples of impersonation scams, our guide highlights the tactics scammers use to trick people in different scenarios.
13. Rogue Security Software (Scareware)
In scareware attacks, scammers use fake antivirus alerts to convince you that your computer is infected and then offer to “fix” it, usually by installing malicious software or asking for a fee.
Example: A pop-up claiming your system has a virus and urging you to install a “free” tool, which ends up stealing your data.
These are only some of the numerous social engineering attacks scammers employ in order to trick people. They have become smarter in their tricks, which is why it is more necessary than ever to be aware and understand what to be more attentive to.
How to Spot Social Engineering Scams Before They Trick You?
Most scams don’t start with a money request. They start with little behaviors that feel slightly odd but not enough to trigger an alarm. These small moments are actually the biggest clues. When you learn to trust those early instincts, you protect yourself long before the scammer can get close. Spotting these red flags early is often enough to stop the scam before any damage happens.
|
Red Flag |
What It Means |
Why It’s Dangerous / How It Helps You |
|
1. Trying to Take You Off the Platform |
The person wants to shift the conversation from Instagram, Facebook, LinkedIn, or Tinder to WhatsApp/Telegram. |
Scammers avoid monitored platforms. Spotting this early helps you pause and protect yourself because genuine people don’t fear accountability. |
|
2. Asking for Account Screenshots |
They ask for wallet balances, bank screens, OTP messages, or login pages under the excuse of “helping” or “verifying.” |
They’re collecting data to break into your accounts. Recognizing this protects your financial identity before they hijack it. |
|
3. Pushing Unusual Payment Methods |
They insist on crypto, gift cards, UPI to unknown names, or P2P transfers instead of proper payment channels. |
Scammers use methods that can’t be traced back to them. The moment you spot this, you avoid irreversible losses. |
|
4. A Profile That Looks Too Perfect |
Photos look polished or AI-generated, with mismatched details, strange shadows, or inconsistencies. |
Catching this early stops emotional manipulation because the person you’re talking to may not exist at all. |
|
5. Sudden Urgency or Pressure |
They use high-pressure lines like “Act now,” “Limited time,” or “Your account is at risk.” |
Urgency shuts down logical thinking. Recognizing this gives you time to breathe, think, and avoid being rushed into a trap. |
The better you know these signs, the easier it is to follow your instincts. Now that we are familiar with the outer things, we will get down to the inner: the psychology scam artists make people fall into, without their knowing it.
How Scammers Trick You: The Psychology Behind Their Tactics
Every successful scam has one thing in common: psychology. Scammers understand human emotion better than most people. They rely on trust exploitation, emotional manipulation online, and persuasion tactics that work on almost anyone, not because victims are unaware, but because the methods are designed to bypass logic.
Here’s the psychology they depend on:
-
Authority Bias: The Confidence Trap
If someone claims to be from your bank or shows an ID, your brain naturally relaxes. Scammers use this instinct by pretending to be professionals. The confident tone and convincing documents make people feel safe, exactly what scammers want before asking for money or private information.
-
Social Proof: Strength in Numbers
People rarely doubt something that looks popular. Scammers create fake buzz around themselves using fabricated profits, comments, reviews, and screenshots. When something looks successful, it’s much easier to believe it’s real.
-
Reciprocation: The “I Owe You” Feeling
Scammers sometimes spend days or weeks “helping” you first. They explain investments, offer emotional support, or share tips. Once a small bond is formed, victims often feel guilty saying no when the scammer finally asks for something in return.
-
Scarcity & Fear: The Panic Button
Fear makes people act fast. Phrases like “limited time” or “your funds are at risk” are designed to trigger panic. When the emotional brain takes over, the logical brain goes offline, and that’s exactly the window scammers use.
-
Emotional Grooming: The Long Game
This is the hardest tactic to spot. Scammers build trust slowly, often sounding caring, consistent, and comforting. They mirror your personality, learn your routines, and create a connection that feels genuine. By the time they make a financial request, the emotional bond is already strong.
Outsmarting Social Engineering: Stay One Step Ahead
Social engineering frauds will not go away in a single day; however, being aware of their mechanisms will leave you much more secure on the internet. When you recognize the emotional pressure that is associated with such scams, you will be able to identify warning signs before things start to fall apart.
And in case something has already occurred, do not blame yourself. A lot of clever, cautious individuals fall into such traps. The point is to be fast, ask questions, and receive the proper support. When something does not seem right, stop, check the source, and contact Global Financial Recovery before acting.
FAQs (Frequently Asked Questions)
Because the attacker isn’t fighting your computer, they’re influencing your feelings. They make you trust them or panic, and that leads people to hand over information without realizing what’s happening.
It’s all in the delivery:
- Phishing: Email traps.
- Vishing: Phone calls pretending to be someone official.
Smishing: Text messages designed to get a quick reaction.
Yes, and they’re becoming common. A cloned voice can sound almost identical to someone you know. If anything feels off, pause and call the person directly using a known number.
In many cases, yes, especially if you move quickly. Some payments can be halted, and crypto can be traced with the right tools. Don’t wait; change passwords, enable MFA, and report to authorities immediately.
Regular check-ins help more than anything. Show them what scams look like, help them use secure settings like 2FA, and remind them to talk to you before sending money or sharing details with strangers.