
- Cryptocurrency
- April 14, 2025
Scammers are using technology to their advantage, and one of their latest scams is cryptojacking. You, being a crypto user, regardless of whether you are a beginner or have any experience in the crypto market, this threat is real.
Imagine you have your cryptos safely stored in your crypto wallet, only to discover that all your cryptos are stolen, even when you have taken all the precautions to protect them in the first place. You might also find that without new electronic appliances, your energy bills are shooting up.
This article is for every crypto user, regardless of whether they are “Hodling” their cryptos for a short term or a long term. We will shed light on how to avoid becoming a victim to this latest crypto threat.
- What is Cryptojacking?
- How Cryptocurrency Mining Works?
- Types of Cryptojacking Attacks: How Hackers Exploit Your Device
- How Cryptojacking Spreads: Common Sources of Cryptojacking Malware
- How to Detect Cryptojacking on Your Device?
- How to Prevent Cryptojacking: Proactive Security Measures
- Case Study: Tesla's Cloud Cryptojacking Incident (2018)
- Conclusion
What is Cryptojacking?

Cryptojacking means scammers have access to either your crypto wallet or use the computing power of your electronic device. While the former involves stealing all your cryptos without your knowledge, the latter uses the computing power of your device to illegally mine cryptos.
As per the Chainalysis report, the number of victims increased from 282 in 2023 to 303 in 2024, with a staggering $2.2 billion, a rise of 21.07% from 2023. The real figures are higher, as these are just the official figures that have been reported. Many victims are unaware that they have fallen for such cyber threats.
How Cryptocurrency Mining Works?
Cryptojacking can be best explained in the following points:
- Cryptocurrency mining process involves validating transactions and adding them to the blockchain ledger.
- Crypto mining explained simply miners solve complex algorithms using computing power to earn crypto rewards.
- Legitimate cryptocurrency mining requires permissioned hardware and software setup to contribute to blockchain networks.
- Cryptojacking-driven mining hijacks a victim's CPU without consent, using their system resources to mine cryptocurrency.
- Blockchain mining depends on consensus algorithms like Proof of Work (PoW) to verify and secure transaction blocks.
- How crypto mining works relies on miners racing to solve mathematical puzzles that maintain the decentralized network.
- Cybercriminals profit from cryptojacking by secretly embedding mining scripts in websites or malware to exploit user devices.
- Bitcoin mining requires high-powered ASICs due to the rising difficulty and competitive nature of its PoW mechanism.
- Ethereum mining, before its shift to Proof of Stake, relied heavily on GPU-based rigs for block validation.
- Monero mining remains CPU-friendly, making it a common target for cryptojacking because it's harder to trace.
- The profitability of cryptojacking lies in the free use of victims' computing power and energy without direct hardware costs.
- Understanding blockchain mining helps distinguish ethical crypto generation from malicious exploitation tactics.
- Mining algorithms like SHA-256 and RandomX define how secure and accessible mining is for different cryptocurrencies.
Con artists are quite smart and make use of technology to rip off their victims by Using Blockchain to Verify Trading Platforms and Avoid Scams.
Types of Cryptojacking Attacks: How Hackers Exploit Your Device
You need to know how con artists exploit your devices:
Browser-Based Cryptojacking
- Cryptojacking scripts embedded in malicious websites or online ads:
One of the common cryptojacking attack types involves malicious scripts hidden in ads or web pages, enabling browser-based cryptojacking without user consent. - How users unknowingly contribute to crypto mining just by visiting a site:
In browser-based cryptojacking, users unknowingly power crypto mining by merely accessing a compromised site—one of the stealthiest types of cryptojacking.
File-Based Cryptojacking
- Cryptojacking malware installed directly onto devices:
File-based cryptojacking, a major cryptojacking attack type, involves installing malware that hijacks your device’s CPU to mine cryptocurrency in the background. - Persistent attacks that continue mining until removed:
This type of cryptojacking silently operates until detected and removed, making file-based cryptojacking one of the most persistent forms of attack.
It is important to protect your crypto from Fake Crypto Wallet Scams.
How Cryptojacking Spreads: Common Sources of Cryptojacking Malware

To better understand how these cyber threats take place, you need to understand how they carry out these threats in the first place
Phishing Emails
One of the top ways cryptojacking spreads is through phishing emails containing crypto mining trojans as hidden attachments. These attacks are classic examples of cryptojacking phishing, tricking users into installing malware unknowingly.
Malicious Websites & Ads
Cryptojacking malware sources often include infected websites or ads that secretly run crypto mining scripts in your browser. Visiting these infected websites' crypto mining operations can unknowingly turn your device into a mining tool for hackers.
Unsecured Public Wi-Fi Networks
Using public Wi-Fi can expose users to cryptojacking malware sources as hackers exploit unsecured networks. This method shows how cryptojacking spreads silently across devices without needing direct downloads or interaction.
Compromised Cloud Services (Charles Parks (CP3O), 2024)
In December 2024, Charles O. Parks III, known as "CP3O," pleaded guilty to wire fraud for operating a large-scale cryptojacking scheme. He defrauded cloud computing providers of over $3.5 million in resources to mine nearly $1 million in cryptocurrency.
It would help you immensely if you have the right knowledge about Email Phishing Scams to avoid falling victim.
How Cryptojacking Works: Step-by-Step Attack Breakdown
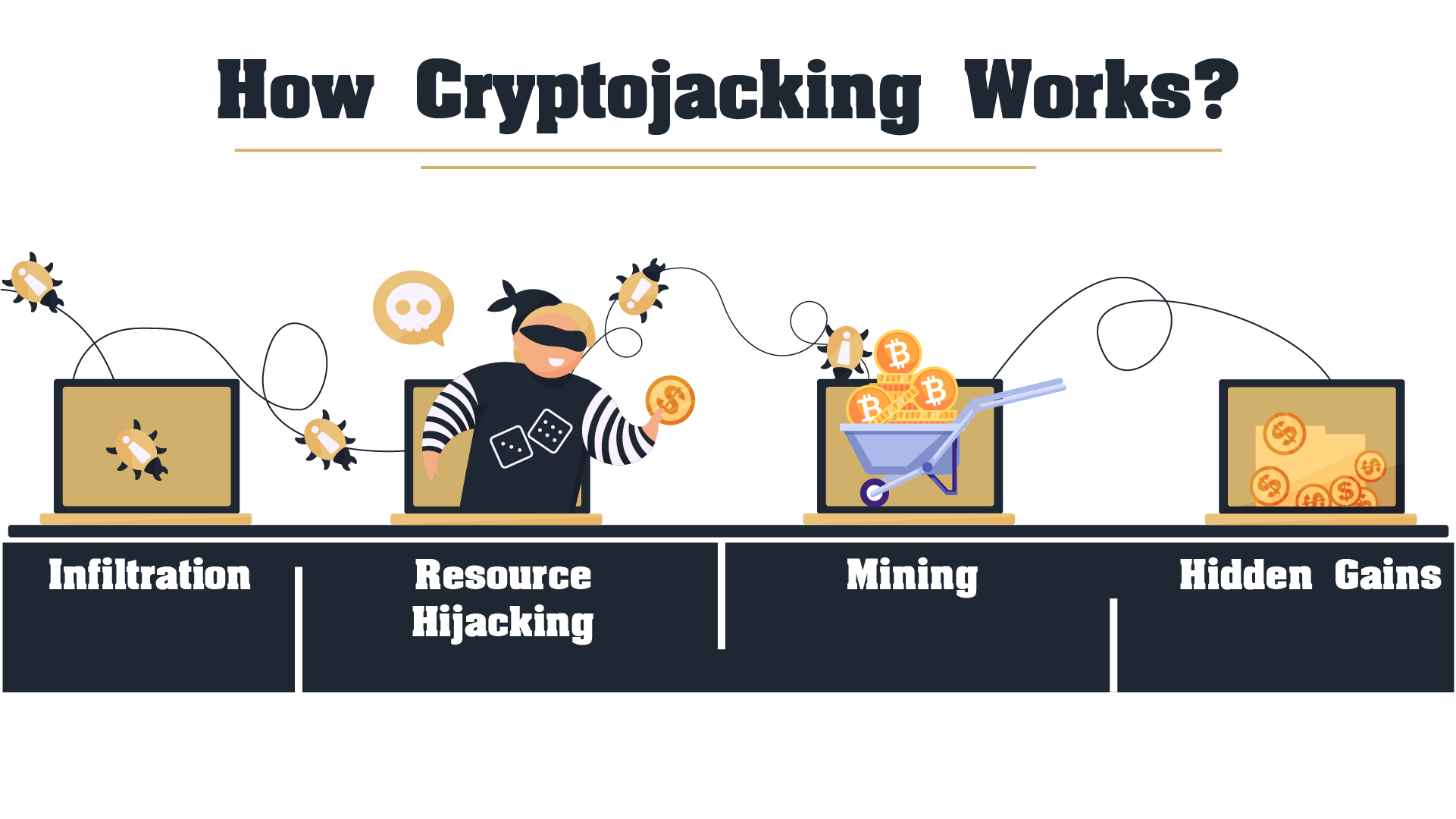
Let’s learn the several steps of Cryptojacking.
Step 1:
Infiltration: Attackers gain unauthorized access to a victim's computer or server, often through phishing emails, malicious downloads, or exploiting vulnerabilities.
Step 2:
Resource Hijacking: Once the system is compromised, the malware takes control, secretly tapping into the device's computing power to mine cryptocurrency, all while the user remains unaware.
Step 3:
Mining: The malware uses the compromised system's resources to solve complex mathematical problems, mining cryptocurrency without the user's knowledge.
Step 4:
Profit: Mined cryptocurrency is transferred to the attacker's digital wallet while the victim experiences degraded system performance and increased energy consumption.
It might surprise you how scammers and hackers rip off their victims through AI-Powered Trading Scams.
How to Detect Cryptojacking on Your Device?
It is necessary that you understand cryptomining malware symptoms, as it will help you to take preventive actions.
Warning Signs
We have mentioned below warning signs that can alert you if you have fallen victim to a cryptojacking scam.
- Slow Device Performance
Notice your system crawling with no clear reason? Slow performance is a common sign of cryptojacking—stay alert for cryptomining malware symptoms.
- Unusual CPU/GPU Spikes
Random CPU or GPU surges without heavy usage? It could be cryptojacking detection in action—one of the clearest signs of cryptojacking.
- Overheating & Battery Drain
Frequent overheating or sudden battery drops? These are classic cryptomining malware symptoms and a key part of how to detect cryptojacking early.
- High Electricity Bills
Skyrocketing energy costs with no new appliances? Unseen cryptojacking activity may be to blame—watch for these cryptojacking detection red flags.
Task Manager / Activity Monitor Analysis
Unusual CPU usage spikes in Task Manager or Activity Monitor can be key signs of cryptojacking, helping with early cryptojacking detection.
If your system slows down and shows high resource use without cause, it's time to learn how to detect cryptojacking through system monitoring.
Browser Extensions: No Coin, MinerBlock
Install browser tools like No Coin or MinerBlock to block scripts—an effective first step in cryptomining malware symptom prevention.
These extensions enhance cryptojacking detection by automatically stopping suspicious crypto-mining activities in real time.
How to Prevent Cryptojacking: Proactive Security Measures
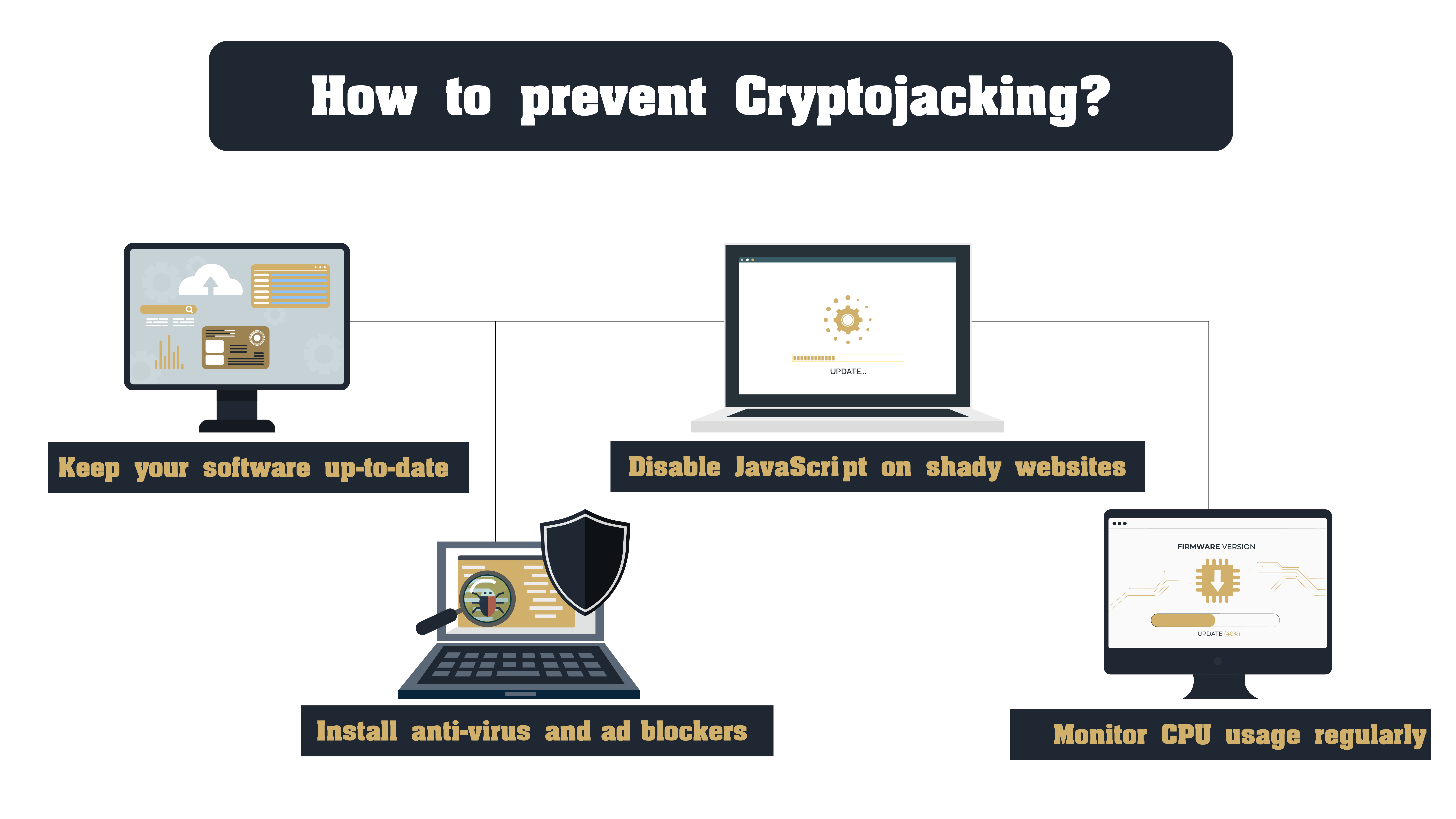
You can follow these cryptojacking prevention tips to avoid falling for such cyber threats:
- Regularly keep your software up-to-date.
- Installing reliable anti-virus and ad blockers
- Disabling JavaScripts on unreliable and shady websites will further block cryptojacking.
- Regularly monitor your CPU usage while browsing the internet or when you turn on your device.
Scammers entice their victims not only through cryptojacking but also through Investment Scams on WhatsApp and Telegram.
Case Study: Tesla's Cloud Cryptojacking Incident (2018)
In 2018, Tesla became a target in one of the most notable real-world cryptojacking cases. Hackers exploited their unsecured cloud system, launching a covert Tesla cryptojacking attack. This cloud cryptojacking attack used Tesla’s resources to mine cryptocurrency undetected. The incident highlighted critical gaps in cloud security and emphasized the growing threat of cryptojacking in corporate environments.
What Happened?
In one of the most notable real-world cryptojacking cases, hackers compromised Tesla’s cloud systems to mine cryptocurrency undetected.
How Was It Detected?
The Tesla cryptojacking attack was uncovered by security analysts who spotted abnormal CPU usage patterns linked to unauthorized mining activity.
Lessons Learned:
This cloud cryptojacking attack revealed that even industry leaders must prioritize cloud security to prevent costly and covert breaches.
Also Read: Learn about other crypto scams in our Crypto Scam Case Studies.
Conclusion
Cryptojacking is a silent but dangerous cyber threat that can drain system resources, inflate operational costs, and expose organizations to broader vulnerabilities. As part of a comprehensive cryptojacking summary, it's clear that implementing layered defenses, monitoring system performance, and training employees are vital steps to protect against cryptojacking. Ignoring this covert threat only empowers attackers to operate longer and deeper within compromised networks.
Early detection and proactive security measures are not just important—they are essential to combating the stealthy rise of cryptomining attacks. To effectively protect against cryptojacking, organizations must deploy real-time monitoring tools, enforce strong authentication, and invest in advanced cryptomining malware protection. Staying ahead of these threats is the key takeaway from any serious cryptojacking summary.
FAQs (Frequently Asked Questions)
Cryptojacking malware secretly uses your device’s power to mine cryptocurrency, often slowing performance. For a summary and to protect against cryptojacking, use trusted cryptomining malware protection tools.
Unusual CPU spikes or slow performance may signal cryptojacking—malicious cryptomining malware using your system. Use cryptomining malware protection tools to detect threats and protect against cryptojacking effectively.
Cryptojacking hijacks your device’s resources for hidden mining, slowing performance and risking data breaches. Use cryptomining malware protection tools to detect threats and protect against cryptojacking. Stay informed with a cryptojacking summary to recognize early signs.
Yes, cryptojacking can affect mobile devices by secretly using their power to mine cryptocurrency. For a quick cryptojacking summary: It drains the battery and slows performance. To protect against cryptojacking, use trusted apps and enable cryptomining malware protection tools.
To remove cryptojacking malware, use trusted antivirus software with cryptomining malware protection and reset affected browsers or extensions. For a quick cryptojacking summary and tips to protect against cryptojacking, regularly update your system and monitor CPU usage for unusual spikes.
